MEV Myth Buster #3: Sandwich Attacks Still Loom Large Above Traders’ Heads
It gets worse when attackers work with builders.
🦄Myth
Private mempools, smart routing, MEV blockers—these protections make us feel like it’s a problem of the past.
But on March 12th, our EigenPhi dashboard told a very different story.
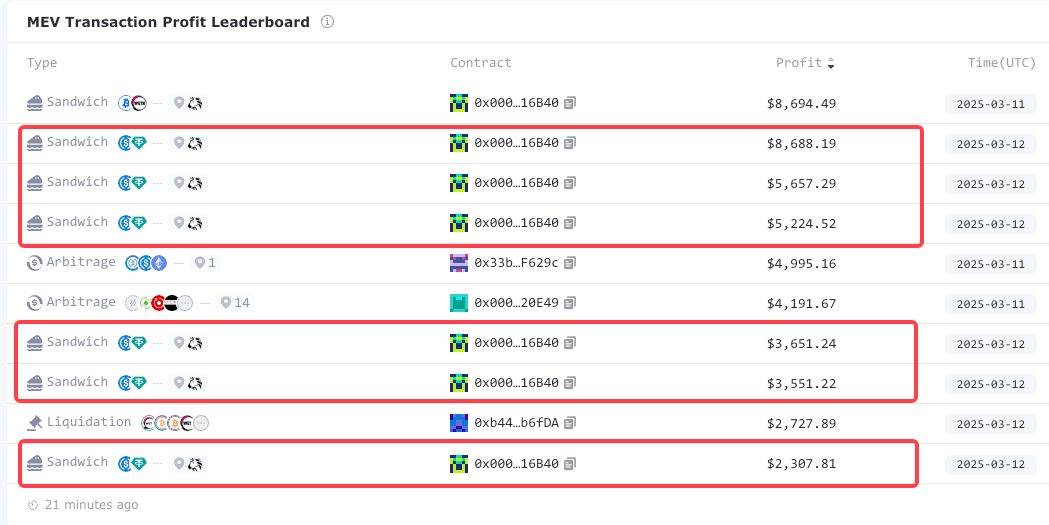
🧠 What Happened
On 12 Mar 2025, the integrated bot-and-builder duo (6B40 + “bob-the-builder”) borrowed millions via Aave to run six back-to-back USDC→USDT sandwich attacks in five minutes, ripping off $714K from one single victim’s six public mempool swaps with zero slippage settings.
🔬Microstructure
The token flow chart below showcases the sandwich that made the victim receive just 5,273 USDT for 220,800 USDC.
🧬 Key Steps Breakdown
We will use the sandwich shown above to illustrate the attack pattern.
The victim sent their intent – swap 220.8K USDC for USDT - to the public mempool. However, while using Uniswap V3’s Router, based on the transaction detail on Blocksec’s phalcon, the slippage of the swap, sqrtPriceLimitX96, was set to 0, telling everyone that it would accept any swapping price.
Upon detecting the victim's swap intent in the mempool, in the FrontRun, the searcher 6B40 borrowed 1.1 million USDC from Aave using 701 WETH as collateral. They then used Uniswap’s flash-loan-like flash swap feature to exchange 18.65 million USDC for 17.58 million USDT between a Curve pool and the Uniswap V3 pool, significantly altering the rate of USDC/USDT in the Uniswap V3 pool.
The price distortion caused the victim to receive only 5,273 USDT in the Victim Transaction.
In the BackRun, 6B40 repaid their Aave debt and secured an $ 8,700 profit, tipping "bob-the-builder. eth" 100.6 ETH, while the user lost $204K miserably.
🧑🤝🧑Key Entities
Sandwich bot 6B40 is integrated with the builder of the block - "bob-the-builder. eth."
🔁 Not a Fluke
The attack we showed above wasn’t random mempool sniping.
It’s the same builder who built all six blocks containing these six attacks: bob-the-builder, detailed in this post.
That explains another anomaly: each block contained fewer than 30 transactions, far below the expected 150+.
Regular users were squeezed out, while the bot got an exclusive lane to execute sandwiches with guaranteed priority.
During a Twitter Space with Ben from BTCS, we highlighted a broader trend:
Over the past year, integrated builder-searcher alliances have surged, while smaller builders are disappearing.
This isn’t just about MEV extraction anymore—it’s about control of blockspace, and who gets in.
So here’s what this case makes clear: sandwich attacks haven’t disappeared—they’ve evolved. They’re automated, systematic, and now privately executed inside builder-searcher partnerships.
And even with today’s best tooling, one bad setting—like zero slippage—can turn you into a farmable pattern.
Because in the new MEV meta, you don’t just get sandwiched once.
As to the victim of these six sandwiches, our research shows that they learned the lesson and set the right slippage the next day while swapping $1 million worth of assets.
⚠️ Your Takeaway
Zero-slippage = zero protection.
Searcher-Builder integration drives small builders away with insatiable appetites and incomparable profits.
Read the first 2 of the MEV Myth Buster Series.
You can click this link or open https://bit.ly/hfdefi to download the free ebook Head First DeFi, Decoding the DNA of Crypto Transactions & Strategies. We are adding more intriguing cases in 2024. Let us know if you want to be part of it.
Follow us via these to dig more hidden wisdom of DeFi:
EigenTx | Website | Discord | Twitter | YouTube | Substack | Medium | Telegram