MEV Myth Buster #2: Adding Liquidity Is NOT Safe From Sandwich Bots
Inside the $851 K “LP-Ambush” that front-ran, skewed prices, and drained a whale
🦄Myth
Most DeFi users think only active traders get sandwiched—swap too much slippage, and you pay the price.
But this case proves: even liquidity providers can be ambushed.
🧠 What Happened
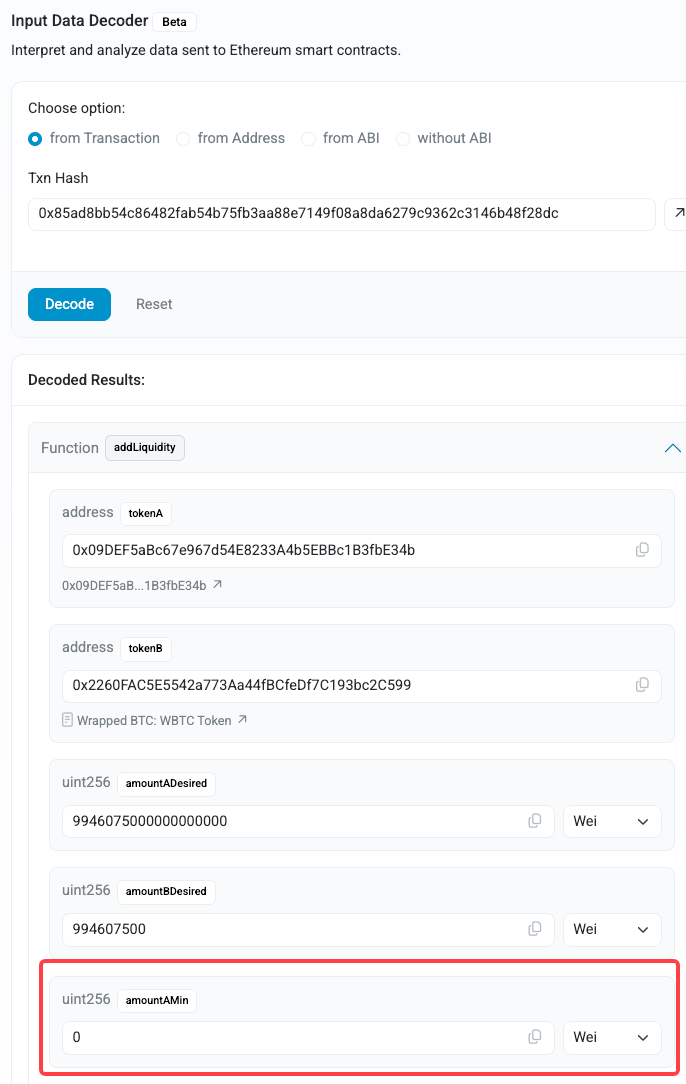
A whale tried to add 9.95 wBTC ≈ $851 K to a Uniswap V2 pool.
One searcher smelled blood, front-ran the deposit, distorted the price, let the LP transaction execute at the skewed ratio, then back-ran the pool to reset prices—walking away with all the wBTC the whale brought to the party.
Zero swaps by the victim.
Full sandwich by the bot.
🔬Microstructure
🧬 Key Steps Breakdown
While adding liquidity to the pool, the whale skipped one essential step: under Uniswap V2, liquidity providers must set AmountAMin, the minimum token amount they will accept.
By omitting this, the LP effectively told the protocol:
“I’ll accept any ratio—even if the price shifts right before my deposit.”
That invitation was all the MEV bot needed.
Step 1: The front-run.
A bot spots the pending LP transaction in the mempool and executes a massive swap just before it. This skews the pool’s price so that WBTC appears cheaper than the paired token.
Step 2: The LP deposit.
The victim adds their WBTC and waBTC into the pool while its price is still distorted. Because the pool overvalues the paired asset, the LP’s contribution is imbalanced: only a tiny amount of waBTC was accepted.
Step 3: The back-run.
The attacker reverses their initial swap—restoring the pool’s true price and locking in the difference as pure profit.
Result? The LP lost $851,000—despite never making a swap.
🧑🤝🧑Key Entities
Sandwich Bot 0xe2c is still actively targeting DeFi users.
Contract 0x3bf, shown in the token flow, is used by 0xe2c as the proxy to execute attacks.
🔁 Not a Fluke
This wasn’t a bug or a code flaw.
It was a legit, on-chain exploit, driven entirely by front‑run and back‑run logic leveraged against an unprotected LP action.
Modern sandwich bots don’t just target traders; they also aim to exploit anyone moving value on-chain without the necessary safeguards.
If you’re adding liquidity, don’t assume safety by default.
In Ethereum’s block-by-block battleground, even builders can get sandwiched.
The following post dives deep into the mathematics of LP-ambush.
Stay vigilant. Stay protected.
⚠️ Your Takeaway
Always set AmountAMin (or your protocol’s equivalent).
Use private RPC relays like Flashbots Protect or MEV Blocker.
Treat LPing like swapping with slippage tolerance—because skipping protections can cost you more than a trade.
Read the first post of the “MEV Myths Buster” series.
MEV Myth #1: Why Your Passive Limit Orders Are Actually Active Targets
If you’ve spent any time onchain, you’ve seen the whispers:
You can click this link or open https://bit.ly/hfdefi to download the free ebook Head First DeFi, Decoding the DNA of Crypto Transactions & Strategies. We are adding more intriguing cases in 2024. Let us know if you want to be part of it.
Follow us via these to dig more hidden wisdom of DeFi:
EigenTx | Website | Discord | Twitter | YouTube | Substack | Medium | Telegram