How to Unveil Jaredfromsubway.eth's Trading Tactics?
Our EigenTx tool now simplifies multi-transaction analysis in one easy-to-understand chart!
Attention! Based on our analysis, Jaredfromsubway.eth's MEV bot rakes in $6.3 million in three months.
DeFi enthusiasts and traders, are you still struggling to make sense of the complex transactions involved in Jaredfromsubway.eth? Let’s use a sandwich cooked by “Jared” as an example to show you how he did it step by step. We will employ our EigenTx transaction visualizer to examine all the token flows.
Once you understand the general idea, you can use EigenTx’s multi-tx combining feature to step up your crypto game!
To better dive into Jared’s strategies to launch the sandwich attack, let's first start with the roles involved in this series of transactions. For the sake of clarity, we set the direction of the token flow charts as TB(Top to Bottom). Click here to find out more about our EigenTx visualizer.
Addresses
From address in the FrontRun transaction and BackRun transaction: an EOA (Externally Owned Account) account, which is Jared’s wallet address in this case: 0xae2Fc483527B8EF99EB5D9B44875F005ba1FaE13.
To address in the FrontRun transaction and BackRun transaction: the contract being Jared’s sandwich bot with the address as 0x6b75d8AF000000e20B7a7DDf000Ba900b4009A80.
The first victim in Victim 1 transaction: 0x831F77bB13a31c5a908c723f8ddfc9193aFA1B05
The second victim in Victim 2 transaction: 0x723B53EFC9B5e76fA9Ddff2ed14Fbe572D212C7a
Protocols
To in the victim transactions: marked as UniswapV2Router02, the trade router provided by Uniswap V2 for routing users’ orders to the matching liquidity pool.
UNI-V2 (Red) in the Front Run, Victim 1 transaction, and Back Run: 0xb9B824fDa6c0C1AFE105d892c24ca21264c77f0a (Click to view its MEV profile), a liquidity pool on Uniswap V2 trading WETH and MPEPE.
UNI-V2 (Orange) in the Front Run, Victim 2 transaction, and Back Run: 0x7054b0F980a7EB5B3a6B3446F3c947D80162775C (Click to view its MEV profile), an liquidity pool on Uniswap V2 trading WETH and MONG.
Tokens
WETH: WETH is an ERC-20 token on Ethereum that represents 1 Ether (ETH).
MPEPE: MicroPepe, a meme coin.
MONG: MONGCoin, the meme coin of MongMob.
How It Works
FrontRun Transaction
TxHash: 0xe99b5e1d1b21954e6e4b14f60fb71acc24913fa07162c941c9e81dc622fd798a
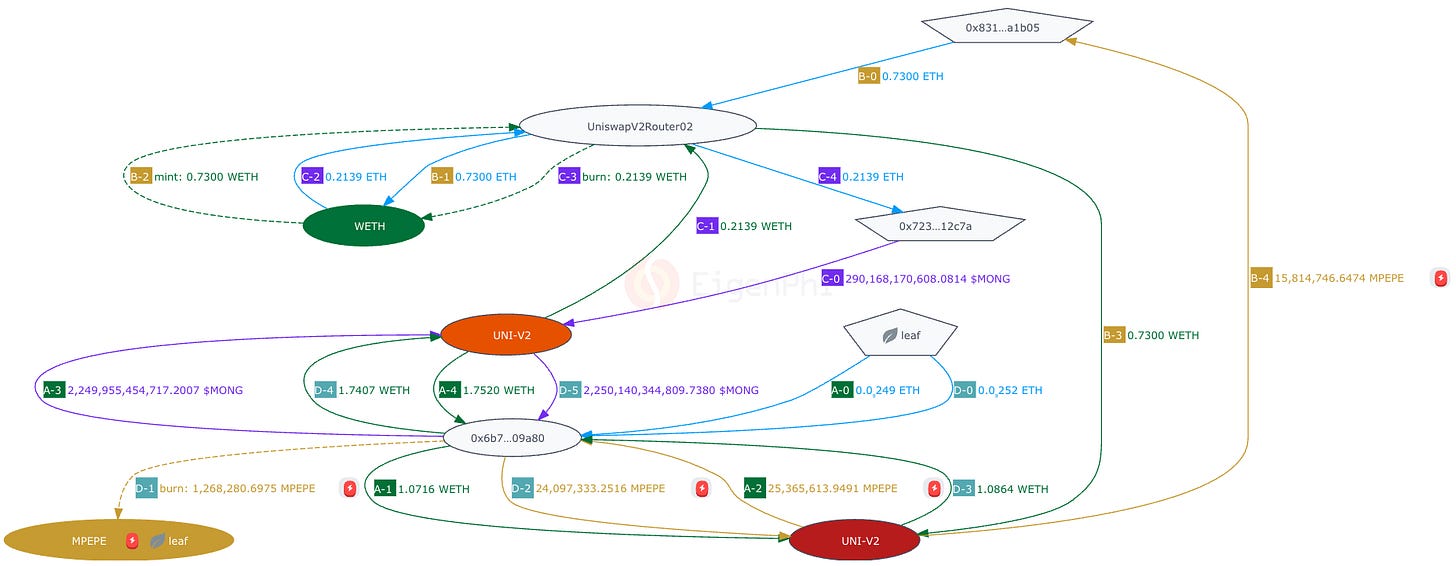
Jared (the "from") discovered 2 victims' transaction intents in the public mempool: "from WETH to MPEPE" and "from MONG to WETH," sent out 0.000000000249 ETH to activate his Sandwich MEV bot. (Step 0)
Then, the sandwich bot 🤖 exchanged 1.0716 WETH for 25,365,613.9691 MPEPE in UNI-V2 (Red) to raise the price of MPEPE against WETH. (Steps 1-2)
Then, the sandwich bot 🤖 exchanged 2,249,955,454,717.2007 MONG for 1.7520 WETH in UNI-V2 (Orange) to raise the price of WETH against MONG. (Steps 3-4)
After these transfers (Steps 0-4), Jared impacted the prices in the pools as:
“WETH to MPEPE”: 1:23,671,083.10;
“MONG to WETH”: 1:1,284,237,554,553.29.
Victim 1 Transaction
TxHash: 0x694feff41ce0f1e8d4f419c92fdd1b0d60ba654a423fafa7a465ee1bc05958a0
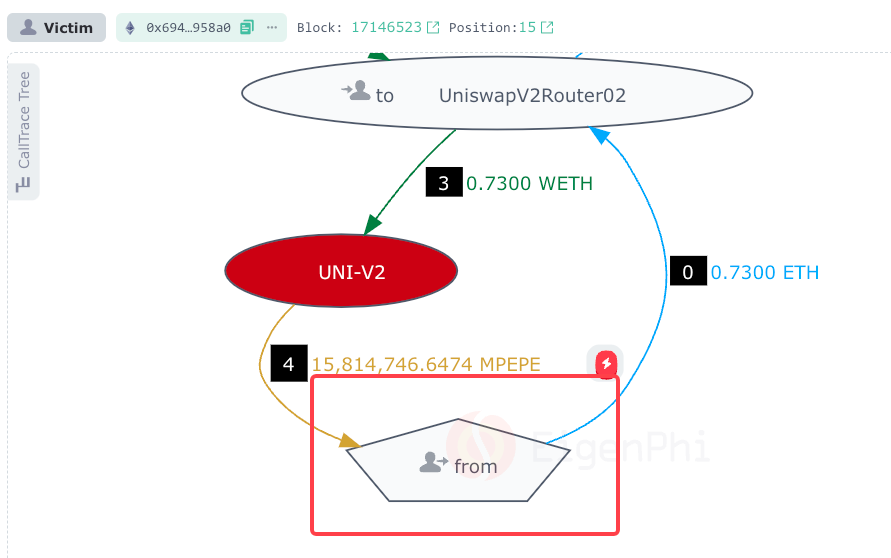
Victim 1 wanted to swap WETH for MPEPE. They sent 0.73 ETH to UniswapV2Router02. (Step 0)
UniswapV2Router02 automatically sent the 0.73 ETH to WrapETH contract and received the 0.73 WETH. (Steps 1-2)
UniswapV2Router02 routed the 0.73 ETH to the UNI V2 pool for WETH/MPEPE pair. (Step 3)
The UNI V2 pool for WETH/MPEPE pair sent the swapped 15,814,746.647432 MPEPE to Victim 1. (Step 4)
After the attacker’s front-run transaction, the exchange price of "WETH to MPEPE" in the Uni-V2 pool was shifted. Then, in this victim's transactions, the victim's price of "WETH to MPEPE" in UNI-V2 (Red) has changed to 1:21,664,036.50, which made the victim receive fewer MPEPE than they should have. (Steps 3-4)
Victim 2 Transaction
TxHash: 0x0379b81ca359ba70a6012aedf8705f250ef053b7867747d1e8bc81fcfd2c5e84
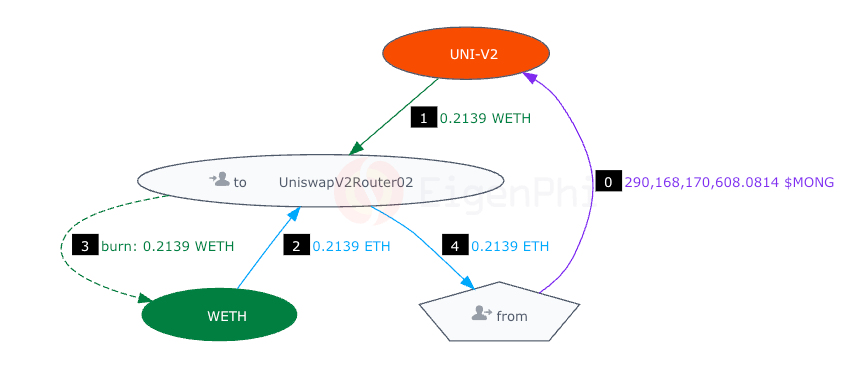
Victim 2 wanted to swap MONG for WETH. They sent 290,168,170,608.08 MONG to the UNI V2 pool for MONG/WETH pair. (Step 0)
The UNI V2 pool sent the resulting 0.2139 ETH to the UniswapV2Router02. (Step 1)
UniswapV2Router02 automatically sent the 0.2139 WETH to WrapETH contract and received the 0.2139 ETH. (Steps 2-3)
UniswapV2Router02 routed the 0.2139 ETH and the victim received the 0.2139 WETH. (Steps 4)
After the attacker’s front-run transaction, the exchange price of "MONG to WETH" in the Uni-V2 pool was shifted. Then, in this victim's transactions, the victim's price of "MONG to WETH" in UNI-V2 (Orange) has changed to 1:1,356,752,936,244.01, which made the victim receive fewer WETH than they should have. (Steps 3-4)
BackRun Transaction
TxHash: 0xfbc01671de8ee2695b6f2d2a7e4dae9580ed30f7b3fdf064fab573da0e9a55ae
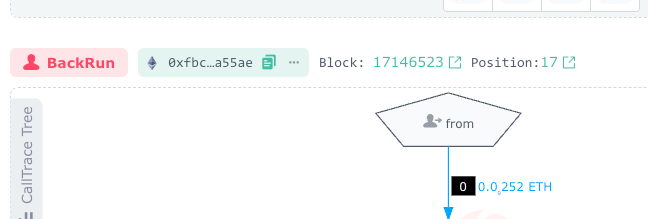
Jared (the "from") sent out 0.000000000252 ETH to activate his Sandwich MEV bot again. (Step 0)
The contract/issuer of the token burnt 1,268,280.6975 MPEPE as a fee. (Step 1)
Then the sandwich bot 🤖 exchanged 24,097,333.2516 MPEPE for 1.0864 WETH in UNI-V2 (Red) at 1:22,180,358.871977. (Steps 2-3)
Then, the sandwich bot 🤖 exchanged 1.7407 WETH for 2,250,140,344,809.7380 MONG in UNI-V2 (Orange) at 1:1,292,646,668,607.8054. (Step 4-5)
To sum up, the attacker 🤖 earned a total of 0.03 WETH and 184,890,092.53 MONG. The total revenue of all the transactions is $49.59. Subtracting the gas fee of $44.35, the sandwich attacker earned $5.24 in total.
Unveil the Full Tactics in One Graph
To better portray strategies involving multiple transactions like Jaredfromsubway.eth’s sandwiches, EigenPhi has introduced the EigenTx multi-tx merging feature, offering a comprehensive transaction visualization. With distinct colors, numbers, and labels to differentiate various trading strategies, users can quickly analyze attackers' and victims' tactics. In addition, our complete transaction information charts provide a convenient way to view several transactions, including MEV data, all in one place!
Where to Find It
When you are using EigenTx to view multiple transactions on the same page, like the mentioned sandwich, you can find the feature as shown in the image below:
Click “View Multi-Txs In One Chart,“ then you can see Jared’s sandwich like this:
In our Multi-Txs, we differentiate multiple transactions by different labels. A, B, C, and D match the four transactions of FrontRun, Victim 1, Victim 2, and BackRun, respectively. And the numbers indicate the order in which the transactions are performed. The same token transfers are marked with the same color line.
To access this feature, simply visit here.
Use EigenTx’s Chrome Extension for More Intuitive Experiences
Moreover, EigenTx is integrated with Etherscan via a Chrome Extension. To enhance your Etherscan experience and learn how to visualize multi-transaction strategies like Jared's, we invite you to check out our tutorial video:
The video features demonstrations of visualizing token flows on Etherscan, checking all related transactions, viewing each token flow separately, and combining all token flows into one.
👀Ready to experience this new feature for yourself?
Visit our website and select "EigenTx" to transform your DeFi analysis.
To get the EigenTx Chrome Extension, visit here.
For more information about EigenPhi, visit here.
🤩Don't miss out on the opportunity to bring clarity to complex transactions like Jared's with EigenTx. Try it for yourself and elevate your DeFi analysis today!
Follow us via these to dig more hidden wisdom of DeFi:
Website | Discord | Twitter | YouTube | Substack | Medium | Telegram