The Tokenomic Trilemma: A Theoretical Framework for Anticipating and Diagnosing DeFi Protocols' Flaws and Risks
And why is it difficult for independently issued algorithmic stablecoins to maintain anchorage and avoid entering a death spiral.
by: EigenPhi Research & Dr. Chuanwei Zou from Wanxiang Blockchain
Key Takeaways:
The token dynamics of blockchain follow the same theory of a tokenomic trilemma: being difficult simultaneously to achieve three conditions of free tradability, anchored price, and independent issuance. This framework guides us in theoretically predicting and identifying possible risky design flaws and upcoming exploits in advance.
Current DeFi protocols may not place enough value on liquidity data. There is a real need for detecting risk precursors by monitoring early liquidity anomalies.
The trend of high leverage, liquidity risk, and maturity mismatch issues requires new solutions.
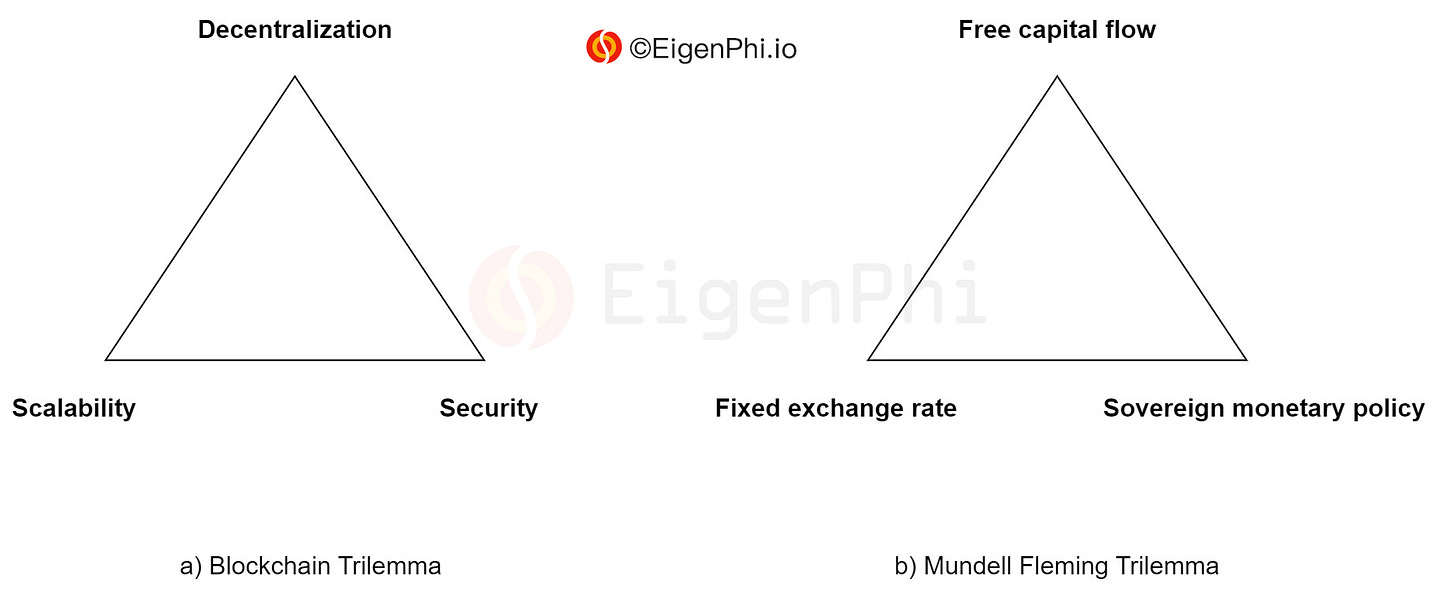
When evaluating and comparing the various blockchain protocols, one refers to the Blockchain Trilemma in describing the challenge of simultaneously achieving scalability, decentralization, and security at the base layer (Fig. a). Furthermore, in discussing algorithmic stablecoins, it is common to cite another impossible trinity in international economics (i.e., the Mundell Fleming Trilemma) to illustrate the difficulty of implementing such a new asset type (Fig. b).
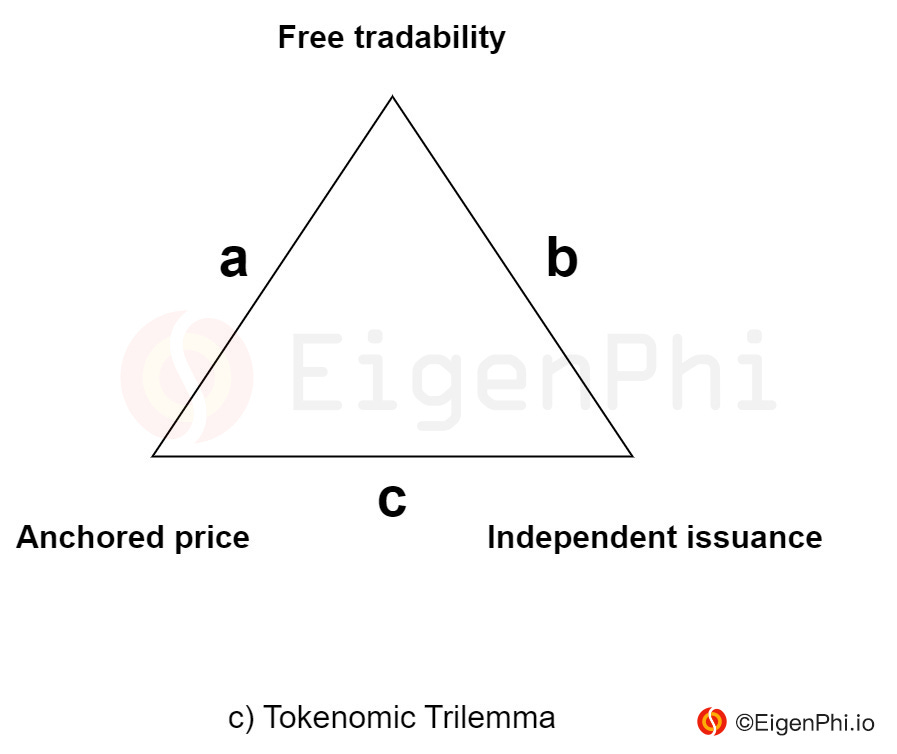
As an extension of the Mundell Fleming Trilemma model, we can abstract the root cause of many risk problems of DeFi, and cross-chain protocols as a tokenomic trilemma: A token has a trilemma in simultaneously achieving three conditions of free tradability, anchored price, and independent issuance (Fig. c).
Case studies
So far, we have found that apart from risk cases caused by technical flaws, most of the risk events of DeFi and cross-chain protocols can be grouped into five categories and depicted by the tokenomic trilemma as we proposed above.
For a token satisfying state a, the arbitrage mechanism realizes the anchored price, which regulates the token issuance. While Category 2 has no false issuance of tokens, the attacker breaks the anchored price condition by manipulating market liquidity and uses the price deviation to launch an attack before the arbitrage mechanism restores the price anchoring relationship.
Category 1: Attacking the token's issuance mechanism
In the first category, the protocol's issuance mechanism is under attack, decoupling the token's price from its anchor.
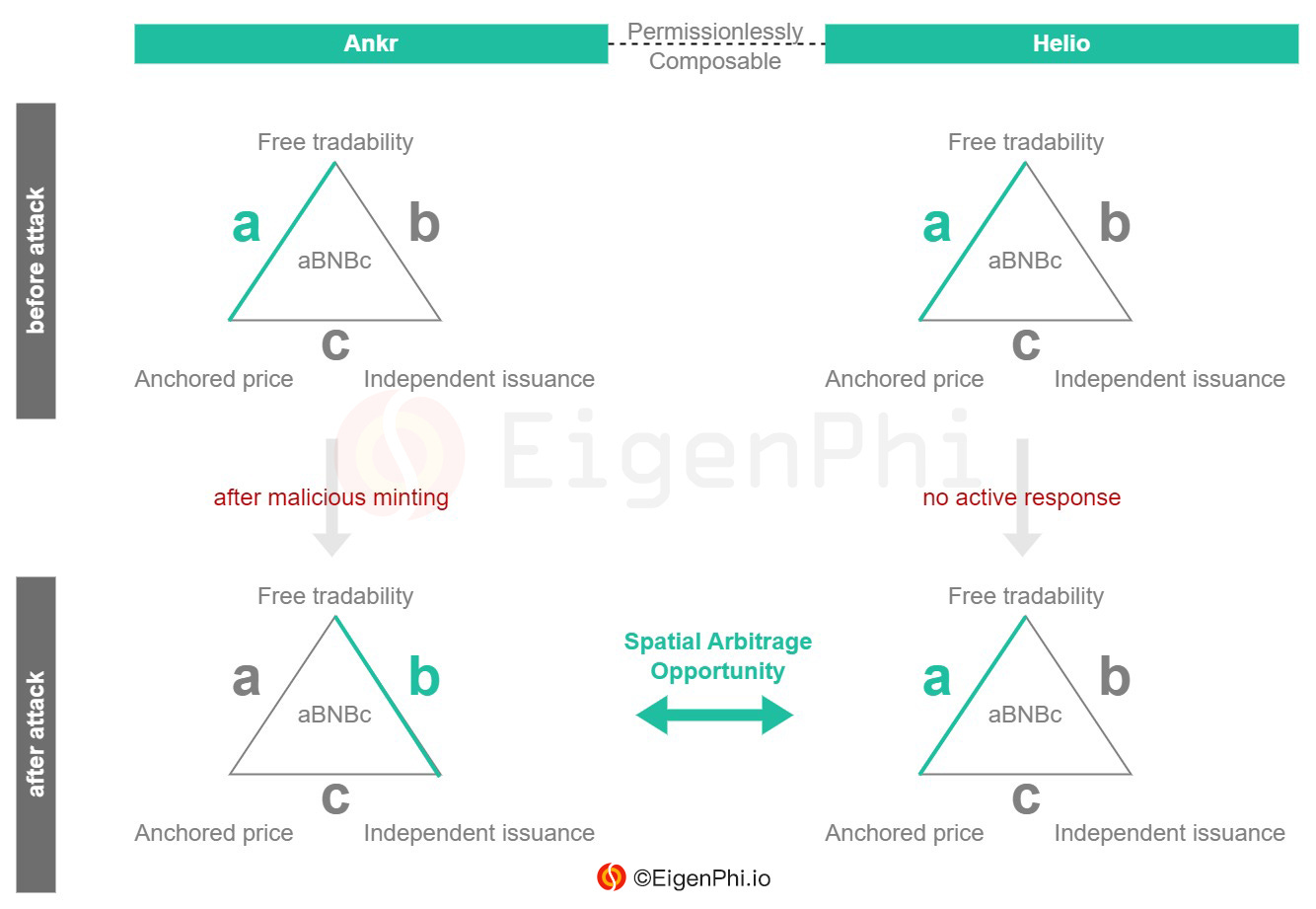
For example, on December 2nd, 2022, BSC platforms' Ankr Protocol was attacked. The perpetrators maliciously issued its liquidity staking token aBNBc. Meanwhile, the arbitrageurs took advantage of the Helio lending protocol, which is permissionlessly composable to Ankr.
💡Case Study: Ankr protocol's private key breach
Ideally, the Ankr protocol issues aBNBc in equal volume based on the user's pledged BNB, i.e., it satisfies the anchored price and free tradability conditions, forgoing independent issuance.The attacker's malicious issuance of aBNBc breaks the original issuance rule of the Ankr protocol, causing the protocol to transit from state a to b in the framework of the tokenomic trilemma, and the new state no longer satisfies the anchored price condition.However, Helio protocol still bases their evaluation of aBNBc on the assumption of the anchored price in the original state a. The arbitrageur takes advantage of the situation when the token has already switched to state b.
Several other cases in 2022 could also be included in this category. For example, in the Lodestar Finance hack on Arbitrum, the problem token, plvGLP, is a collateral asset adopted by the Lodestar lending protocol and a voucher token representing the staked assets in Plutus DAO. The attacker exploited a smart contract vulnerability to manipulate the issuance mechanism of plvGLP, causing its price anchoring its AUM value to be maliciously inflated, thereby over-lending a large volume of assets out of Lodestar. The Wormhole bridge attack can be described similarly.
Category 2: Manipulating the underlying token's market liquidity
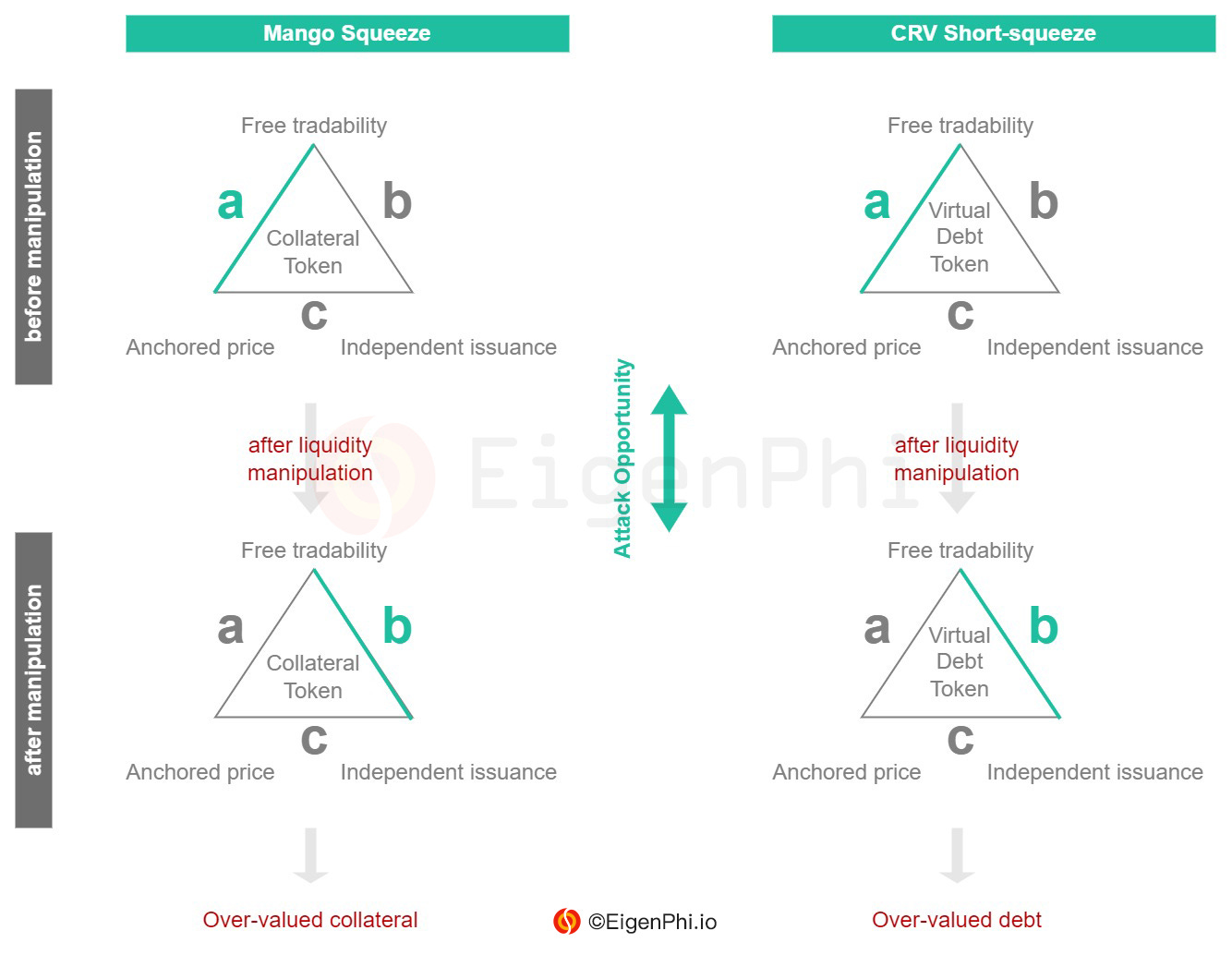
In addition to attacking the token’s issuance mechanism by discovering vulnerabilities, manipulating the market liquidity of a token to control its price can also effectively attack the token economy system. Since Avraham Eisenberg (@avi_eisen), the lead of the Mango Squeeze event, publicly described on Twitter how his team operated a highly profitable trading strategy by manipulating liquidity, liquidity manipulation attacks, sometimes referred to as price manipulation attacks, have generated widespread consideration and discussion in major lending protocols' forums. First, we will show how to use the tokenomic trilemma to explain this risk category. Next, we illustrate the case of Mango Squeeze and the case of CRV Short-squeeze, which generated bad debt on Aave.
In the Mango squeeze event on October 11th, 2022, Avi's team opened a long MNGO-PERP position hedged by a short one in two separate accounts and pledged the long position to the Mango Lending Pool to prepare for subsequent lending. Then Avi's team used approximately $4 million to drive up the price of MNGO more than 22 times on several spot markets. And the lending pool increases the total amount of assets they can lend based on the valuation of the unrealized gain of the collateral MNGO-PERP ($483 million). As a result, the team managed to lend $116 million worth of assets with a principal of $14 million.
(Source: Coingecko & Gauntlet)
In another strategy conducted a month later, Avi dumped the CRV market with 92 million CRV borrowed from AAVE. But he appears to have incurred a loss after facing a precise short squeeze attack, which created a bad debt on AAVE worth about $1.6 million at the time. The short squeezers targeting him pushed the price of CRV so high that Avi's lending position could not be timely liquidated before entering a bad debt situation.
In either case, the attackers attacked the anchored price condition of the collateral token or the virtual debt token by manipulating the underlying token's market liquidity. We note that such attacks always manipulate the valuation of collateral or debt by creating a significant price change in a short period.
💡
Case Study: Mango Squeeze
Before Avi manipulated the spot price of MNGO, the opening price of the long position MNGO-PERP, which the attacker minted, should have been anchored to the current level of market liquidity and the average price of MNGO.After depositing it as collateral in the Mango Lending Pool, the attacker rapidly inflates the spot market price of MNGO, resulting in an abrupt change in the anchored price condition of MNGO-PERP, effectively destroying the robustness of the original price anchoring relationship.Meanwhile, the protocol can't respond to sudden changes in the token's market liquidity and price to correct the corresponding open positions, which is equivalent to switching from state a of the tokenomic trilemma to state b.The attacker pledges assets to the lending platform in state a, and lends excess assets through overvalued collateral in state b.
💡 Case Study: CRV Short-squeeze
Before the CRV short-squeezers pumped the CRV price, Avi had already established a huge lending position in the Aave protocol. To measure the value of this position, we assume that the protocol issues Avi a certain amount of virtual debt tokens representing the lending position, and that Avi must return an equal volume of CRV to destroy these virtual debt tokens.The valuation of Avi's lending position is expected to be based on the virtual debt token's price, anchoring the current level of market liquidity and the average price of CRV.However, CRV longers instantaneously inflated the CRV spot price and, in a similar logic to the Mango Squeeze event, this sudden price change undermined the reliability of the valuation of the lending position by anchoring the underlying token's market price, which is equivalent to breaking the anchored price condition of the virtual debt token.After Avi created the lending position at state a, the short-squeezers attacked him by forcing the virtual debt token changes to state b, which resulted in a sudden increase of bad debt in Avi's lending position.
In addition, depending on the target and the purpose of the attack, the attacker may also make the collateral or debt undervalued by manipulating the market liquidity of the underlying token. Although no false issuance of tokens occurs in this category, the attacker breaks the initial arbitrage condition backing the anchored price by manipulating the market liquidity and uses the price deviation to launch an attack before the arbitrage mechanism restores the price anchoring relationship.
Category 3: Algorithmic stablecoin
The designers of algorithmic stablecoins are trying to create a monetary system run by algorithms. This algorithmic system poses the challenge of simultaneously satisfying the three conditions of the tokenomic trilemma. However, in terms of practical results, from the emergence of the first algorithmic stablecoin NuBits in 2014 to date, there has yet to be a truly successful one that counts as stable.
However, there are still protocols that incorporate some new designs of algorithmic stablecoin emerging one after another. We are not conclusive whether this direction is creating a perpetual motion machine in the token economy. We remind industry participants of the potential crisis that such new protocols can bring to the DeFi system. The negative impact of risk contagion from the UST-LUNA system on the development of the industry should trigger deep thinking among builders.
Category 4&5: Technical flaws
Flaws in the messaging mechanism or security vulnerabilities mainly cause other risk cases not included in the tokenomic trilemma framework. For example, arbitrageurs or attackers have repeatedly utilized the permissionless update feature of price oracles to extract MEV from the protocol. Essentially, they are taking advantage of lagged off-chain information to create and profit from price bias in their favor.
Incidents such as the Ronin Network attack, which has been the number one loss to date, are related to security vulnerabilities that allow hackers to withdraw funds directly to their wallets.
Conclusions and discussion
The tokenomic trilemma offers a theoretical framework for predicting and identifying possible risky design flaws and upcoming exploits in advance.
Through the case study above, we find that the token dynamics of blockchain seem to follow the same theory of a tokenomic trilemma, i.e., there is a trilemma in the three conditions of free tradability, anchored price, and independent issuance. This framework guides us in theoretically identifying possible risky design flaws in advance.
In the scope of DeFi, a widely adopted value proposition is the permissionless nature of token issuance and trading. This means that the condition of free tradability can be satisfied by default in the DeFi ecosystem. Nevertheless, simultaneously meeting the other two requirements of the impossible trinity will challenge this trilemma and produce hidden dangers.
As a result, independently issued algorithmic stablecoins, centralized operated liquidity/synthetic tokens, or those with low safety margins are more likely to face attack vectors. We have already witnessed from historical facts that these token types have experienced frequent risk events in past years.
The significance of liquidity calculation is undervalued.
On the other hand, these cases also reflect an important fact we want to highlight. As exemplified by several liquidity manipulation attacks in Q4 2022, blockchain's liquidity data is open and transparently computable. Searchers are adept at utilizing this to extract value from protocols, yet the protocols are slow to respond to abnormal market changes.
This problem indicates that the current DeFi protocols may not place enough value on liquidity data, resulting in an information gap disadvantage against searchers and attackers. Therefore, we propose that a feedback system based on real-time liquidity sensors is indeed helpful in achieving proactive risk management.
More specifically, it is difficult for independently issued algorithmic stablecoins to maintain anchorage and avoid entering a death spiral. For such tokens, there is a real need for detecting risk precursors by monitoring early liquidity anomalies. For example, the UST collapse in May 2022 was, triggered by its second large-scale de-anchoring, while someone warned about risk on the forum in the previous year when the first de-anchoring occurred. But there is a lack of a more convincing analysis based on factual data to make informed judgments.
For centrally operated or poorly secured liquidity/synthetic tokens, there are risks arising from corruption, security breaches, and other factors that lead to manipulation of issuance and breaking the anchored price condition of the tokenomic trilemma. Meanwhile, long-tail assets are vulnerable to liquidity manipulation attacks to affect the valuation of virtual debt or collateral tokens issued based on this underlying asset.
These risks often correspond to abnormal changes in tokens' circulation or distribution among different addresses. The diverse transaction activities in DeFi are composed of various functions, including the most basic mint(), transfer(), burn(), and more complex business actions such as swap(), borrow(), repay(), and so on. But all these functions ultimately correspond to changes in the address balances. If these parameters are treated as statistical observations, anomalous token flows can be detected by calculating the dramatic changes in the network entropy of token distribution in different addresses.
For example, the massive issuance of aBNBc by the attacker corresponds mathematically to a sharp decrease in the entropy of the trading network of this token. As the liquidity distribution continues to evolve through follow-up transactions, the entropy increases and restores a steady state. Actually, there is a time window between equilibrium states, as found by Helio arbitrageurs. Capturing the changes in liquidity data during this time also helps detect anomalies. The significance of doing so is that we are no longer based on a whitelist and Priori attack patterns.
Other risk events not covered in the tokenomic trilemma framework are related to technical flaws, and we rely on careful protocol design and rigorous code auditing to avoid risks. Nevertheless, whether threats come from manipulating price oracles or stealing private keys to directly withdraw funds, monitoring liquidity data remains a much-needed risk control tool to assist in the discovery of attacks.
Insights on liquidity calculation
DeFi achieves decentralization at the cost of a change in trust mechanisms.
The issuance and circulation of money in traditional finance are based on a relational trust mechanism established on people-related factors such as identity and reputation.
The issuance and circulation of tokens in DeFi are based on impersonal smart contracts and transactional trust mechanisms such as over-collateralization.
Although this transaction-based trust mechanism has the characteristics of decentralization and solves many problems of the centralized operation model in the trading stage, It is not fully superior than the trust-based system of traditional finance.
The liquidity in DeFi is size-limited and volatile.
On the one hand, unlike Bitcoin and Ether, it is increasingly difficult to capture value for native tokens issued independently by new protocols. The total value of these native blue chip tokens based on certain innovational consensus is limited in size.
On the other hand, in the debt issuance stage, the biggest drawback of issuance via over-collateralization is capital inefficiency, which also faces a bottleneck in the scale of lending funds.
Furthermore, the native tokens with independent issuance and free tradability conditions do not easily maintain price stability and are not suitable for serving as a medium of exchange, which has, to a certain extent, given rise to the birth of algorithmic stablecoins and crypto users' reliance on reserve-based stablecoins such as USDT and USDC.
MakerDAO introduced USDC as collateral after the 312 events, essentially introducing centralized credit to increase its debt ceiling and cushion risk capacity.
Liquidity tokens and synthetic tokens are adopted to improve DeFi's capital efficiency and size limit issues.
In mitigating the above problems, a commonly adopted approach is to distribute liquidity tokens based on the underlying asset or issue synthetic tokens anchoring a price function calculating the underlying values.
As the name suggests, liquidity tokens are minted to release the liquidity of tokens being over-collateralized or staked into smart contracts. You can think of them as certificates of deposit obtained after depositing money into a bank. Uniswap's LP token, AAVE's aToken, and Lido's stETH all fall into this category.
The synthetic tokens are not native to the blockchain and sometimes even have an independent issuance mechanism. These tokens usually anchor a combination of other values to mint, burn and calculate the price according to a particular algorithm. But there are also synthetic tokens minted based on just information without collateral.
When DeFi users use liquidity tokens as collateral for lending or mint synthetic tokens as derivatives, it elevates the entire leverage level of the system.
The trend of high leverage, liquidity risk, and maturity mismatch issues requires new solutions.
As DeFi's composability feature rolls out, protocol-to-protocol linkages become increasingly complex. In addition, a growing variety of liquidity tokens and synthetic tokens leads to increased leverage, liquidity risk, and maturity mismatch issues across the system.
Attacks targeting vulnerabilities in the economic system are frequent, and simple security loophole detection is no longer sufficient to counter the threat of attackers.
The tokenomic trilemma gives us a theoretical framework to anticipate protocol design flaws that may be at risk. Unfortunately, some current protocol designs, including algorithmic stablecoins and cross-chain protocols, may be overconfident in challenging the trilemma. We need to be wary of any tokens that claim to be price anchored.
We also need to introduce real-time monitoring of anomalies in DeFi systems based on liquidity data.
We see the dawn of liquidity calculation in DeFi.
It is not easy to calculate liquidity in traditional finance because there is insufficient transparency. The use of smart contracts uniquely positions DeFi to do this because transactions are entirely transparent in both issuance and trading stages, making liquidity calculation in DeFi possible. Simultaneously this also provides the database to design a proactive risk management model.
We all know that the biggest change of DeFi compared to traditional finance lies in the utterly different issuance and trading mechanism, which represents a vast market opportunity for data analysis because it is observable. The mint function creates new tokens, and liquidity increases. The burn function destroys the tokens and liquidity decreases. The trading process, swapping two or more tokens, corresponds to the price discovery of the token. Finally, the lending process increases leverage. These are fundamental points at which we measure liquidity.
Suppose we can express the principles of issuance, trading, and changes in leverage in mathematical formulas and models based on liquidity data. In this case, it is possible to construct a mathematical representation of the DeFi system to measure objectively the risks and opportunities involved.
Follow us via these to dig more hidden wisdom of DeFi: