The Arbitrageur Who Beats Everyone Else in an Hour
The security and robustness cannot be built on the assumption that no one within the system will make a mistake.
Abstract
At block number 23545404 (Dec-02-2022 12:43:18 AM +UTC) on BSC, an attacker successfully packaged a transaction on-chain targeting the liquid staking protocol Ankr's Deployer contract, in which the reward-bearing token aBNBc was suddenly minted at an amount of 10 trillion and transferred to the attacker's address 0xf3a4.
In subsequent transactions, the attackers minted another 50 trillion aBNBc and exchanged only a tiny percent of these printed tokens into blue-chip ones worth $5.656 million via DEXes. Instead, the attacker transferred part of the proceeds to Ethereum via cross-chain bridges and mixed the remainder through Tornado Cash.
According to CZ, the theft of the private key of the Ankr Deployer contract may have caused the attack. Moreover, after the first attacker carried out the exploit, several other participants took the opportunity to profit from it. One of them took advantage of a defect in the Helio lending protocol's evaluation of ankrBNB's value and staked cheaply-purchased ankrBNB to the protocol. This staked ankrBNB allowed him to borrow excess HAY and exchange it for BNB and BUSD via DEXes, totaling $15.533 million (three times the attacker's proceeds). Several DEXes were also affected by a cascading effect.
This article will show that the swift actions of the Helio arbitrageur and the followers demonstrate that searchers perform better than protocols in gathering information and detecting trading opportunities or risks. This event also sheds new light on liquidity. A significant increase in the issuance of a problem asset can be a precursor signal to the sale of the asset into the market and subsequent devaluation.
The arbitrageur was well prepared to take advantage of this delay. Conversely, the affected protocols were unaware of it. Helio's failure to set up a separate oracle for aBNBc to track its market price indicates that the current DeFi protocol's risk control system is careless and unresponsive. We hope to provide some insights to related parties by carefully reviewing the incident's details.
Timeline
The Ankr attacker, as the originator of this incident, naturally deserves attention. On the other hand, various KOLs have also retweeted the story of the Helio arbitrageur, who made 15.5M BUSD with only 10 BNB. Both roles use two new addresses during the event, with historical transaction counts of 78 and 96, respectively. It's interesting to compare them by merging the timeline of both roles' actions. The following table summarizes the timeline of crucial transaction steps for these two addresses.
Ten minutes after the Helio arbitrageur completed the 6th round of arbitrage, implicated protocols, and third-party tools started tweeting security alerts one after another, for example:
2022/12/2 01:55, Wombat Exchange paused the aBNBc pool
2022/12/2 02:13, PeckShieldAlert tweeted the incident
2022/12/2 02:24, Ankr tweeted an announcement
Cashing out a tiny percentage of fake aBNBc
The table above shows that the Ankr attacker minted aBNBc in increments of 10 trillion every six times. However, he converted only 27,074 aBNBc into BNB and USDC, and the attacking address 0xf3a4 still holds over 60 tri llion aBNBc unused at the moment (with an amount of 7,777,777 incoming aBNBc from 0x0d86).
The attacker converted 27,074 aBNBc to 4,050,000 USDC and 5,500 BNB via PancakeSwap, then 4,500 BNB to 1,293,086.99 USDC. They transferred all the USDC to Ethereum via three cross-chain bridges: Celer Network, deBridge, and Multichain, and mixed 900 BNB left in 0xf3a4 via Tornado Cash. The Ankr attacker's total gain was about $5.656 million, with 1 BNB worth $292 at the time.
Six rounds of arbitrage with high ROI
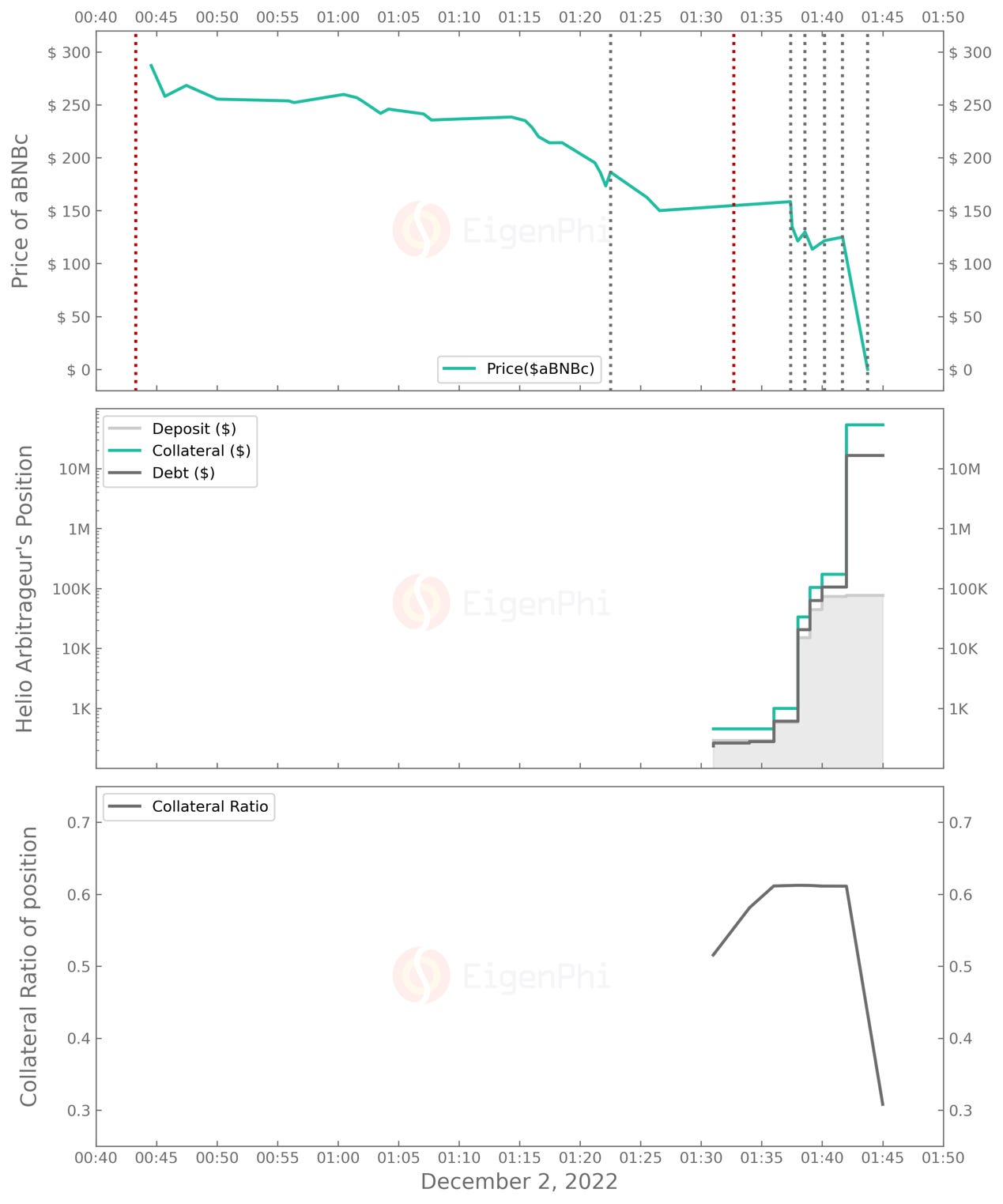
As you can also see from the table above, the Helio arbitrageur activated this new address the day before the Ankr attack and conducted several arbitrage activities between BUSD, MATIC, and WBNB at PancakeSwap. However, just 40 minutes after the Ankr attacker's first mint operation, this arbitrageur quickly reacted and started his first round of testing on his strategy involving the Helio platform.
In the beginning, several of the arbitrageur's transactions reverted due to problems setting the borrowing amount. They waited until they had successfully tested the strategy to gradually increase the principal amount from 1 BNB to 50 BNB and 100 BNB.
Before the 6th round of arbitrage, the price of aBNBc in the DEX market had not completely collapsed, and the swap ratio was above 0.41 BNB per aBNBc. Note that the Ankr attacker converted the last aBNBc into a blue chip token at 01:39:11, when the swap ratio was around $113 or 0.39 BNB per aBNBc
Just 2 minutes after the 5th round, the price of DEX plummeted to near zero. One reason is that many other participants followed the Ankr attacker's action and cashed out more aBNBc.
While everyone else was putting aBNBc into the DEX's liquidity pools to smash its price, the Helio arbitrageur took the opportunity to implement the 6th round of arbitrage. He obtained 183,884 aBNBc for only 10 BNB, at which point the exchange price dropped to 0.00005438 BNB per aBNBc, showing that the DEX's liquidity pools had become severely imbalanced.
Helio's valuation of aBNBc failed to keep up with the market. This price discrepancy allowed the arbitrageur to take advantage of the overvaluation of this collateral. They borrowed 16,444,740 HAY, which they swapped for about 15.5 million BUSD.
After six rounds of arbitrage, the arbitrageur invested a principal amount of 262 BNB and earned a net gain of 15,504,986 BUSD and 97.4438 BNB (not considering the cost of gas fees), equivalent to $15,533,440. The ROI of the 6th round is about 530,800%.
Other interested parties
We also studied some other addresses involved in this incident, including implicated third-party protocols, follow-on attackers who mimicked the Ankr attacker’s minting behavior, and other addresses that profited considerably during this time.
Implicated third-parties
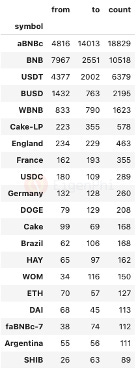
To identify the third-party protocols that also suffered losses in this event, we obtained all transactions that generated aBNBc-related transfer logs during the event, and further extracted all token transfer logs that occurred in these transactions.
In total, we obtained 345,199 token transfer logs. They contain 15,762 unique "from" addresses, 17,793 unique "to" addresses, and 601 unique tokens. We find the top 20 tokens with the highest frequency of interaction with the from address and to address to see which kinds of tokens are primarily involved in this event. aBNBc, BNB, USDT, BUSD, WBNB, USDC, and HAY are all included in the list.
We convert the BNB and WBNB held by the addresses into dollar value based on the price of $292, and calculate the net value change of each address by the net amount change of BNB, WBNB, USDT, USDC, and DAI and omit other tokens' value. We found the following three DEX pools suffered predominantly.
The Helio arbitrageur's HAY sell off affected the HAY related trading pools of PancakeSwap and Wombat. They swapped out most of the BUSD, causing the HAY price to deviate heavily from $1.
Follow-on attackers
The following table lists the addresses that are suspected to have followed the attackers in this incident and profited in the same way. Proceeds are estimated at a price of $292 per BNB/WBNB.
Other winners
In addition, we found several addresses with only net inflows across tokens and ranked high in the total net inflow. One should note that since some of the winners transferred their final proceeds elsewhere, this method will miss such addresses.
Insights
Security
The theft of Ankr Deployer's Private Key caused a security incident. But the security and robustness of the DeFi system cannot be based on the assumption that no one involved in the system can make a mistake. People make mistakes, programs have bugs, and these are all inherent characteristics of the system.
Information monitoring bias
The swift actions of the Helio arbitrageur and other followers demonstrate that searchers perform better than protocols in gathering information and detecting trading opportunities or risks.
He acted quickly after the attacker's first aBNBc minting transaction and before the aBNBc market had collapsed entirely, with ample time to conduct two small-scale tests. A reasonable guess is that his monitoring system observed an anomaly in aBNBc's total circulating amount and succeeded in alerting him to it.
What makes him even better is that he figured out the arbitrage path to pledge aBNBc to Helio and borrow HAY before the market crashed. Then he quickly captured the huge valuation difference between the Helio protocol and other DEXes on the token in question at the moment of the crash. The whole process took him about 1 hour.
Oracle manipulation
For the Helio lending platform itself, it would be unwise to evaluate a reward-bearing token on top of some ideal assumptions (e.g., the probability of aBNBc deviating from BNB is small). Therefore, the relevant protocols should always be alert that there is no absolute anchoring relationship between the values of different tokens.
Protection against abnormal liquidity
Many protocols do not react promptly when extreme events occur in the market and DeFi system. This lack of response resulted in the drain of the Helio lending platform and some DEX pools suffering severe losses.
During the event, there was a delay of hundreds to thousands of blocks between the occurrence of the giant aBNBc mint and the subsequent actions. If this window of time is seized, the risk contagion can be stopped early by closing the market to the risky asset, preventing it from being used as collateral, or adjusting the parameters of how someone can borrow it. As a result, the impact of a security event may be avoided or mitigated.
The current DEX or Lending protocol uses quasi-static parameter settings and is slow to adjust in response. This is why we again emphasize the importance of establishing a dynamic risk control system for DeFi with a feedback loop based on the liquidity state of the market.
Disclaimer
The "Information" contained in this post has been prepared solely for informational purposes, is in summary form, and does not purport to be complete. The Information is not, and is not intended to be, an offer to sell, or a solicitation of an offer to purchase, any securities. The Information does not provide and should not be treated as giving investment advice. The Information does not take into account specific investment objectives, financial situation or the particular needs of any prospective investor. No representation or warranty is made, expressed or implied, with respect to the fairness, correctness, accuracy, reasonableness or completeness of the Information.
We do not undertake to update the Information. It should not be regarded by prospective investors as a substitute for the exercise of their own judgment or research. Prospective investors should consult with their own legal, regulatory, tax, business, investment, financial and accounting advisers to the extent that they deem it necessary, and make any investment decisions based upon their own judgment and advice from such advisers as they deem necessary and not upon any view expressed herein.
*We are open to discussion. Please feel free to contact us via contact@eigenphi.com.
Follow us via these to dig more hidden wisdom of DeFi: