Dominance, Speed, and Million$ Moments: The Vyper Exploit's Liquidity Scramble in the MEV Battlefield
Insights into bot strategies, speed, and profit maximization enable mastery over the MEV battlefield in volatile crypto markets.
Key Takeaways from the MEV Battlefield
In the world of cryptocurrency, the MEV (Maximal Extractable Value) battlefield has revealed some interesting insights about how bots operate during chaotic events like the Vyper exploit. Here are the main points:
Crypto's Gold Rush: Cryptocurrency risk events are becoming treasure troves for MEV bots. The arbitrage revenue on the event day was an order of magnitude higher than the daily average.
Million-Dollar Moments: Elite bots, exemplified by c0ffeebabe.eth, can amass fortunes from a single trade during market volatility. Timing, not constant activity, is their secret.
Furious Competition: Bots now engage in lightning-fast competition, seizing profits within seconds. Smart bots can span across 6 or more pools to discover arbitrage opportunities. Their intelligence and agility continue to evolve.
Profit Disparity: In the attack on the first Curve pool, the top-performing bot outshone its closest rival by a staggering 197-fold.
Speed is Everything: Even seasoned bots can miss out when the competition is fierce. Speed and a robust infrastructure are crucial, no matter how successful you've been in the past.
Squeezing Every Drop: Advanced bots execute multiple back-running moves to squeeze out every last bit of arbitrage value, leaving no opportunity untapped.
Order Flow Advantage: Some bots gain a competitive edge by strategically exploiting privileged order flow, unveiling a hidden weapon.
Integration Matters: Bots with Searcher-Builder integrations show advantages, helping them find and seize opportunities more effectively.
Part 1 - Vyper Exploit Unleashes a Liquidity Scramble
On July 30th, a critical bug was exploited in the Vyper smart contract compiler, enabling attacks on Curve protocol's four liquidity pools one after another. This sparked intense competition between arbitrage bots to profit from the vulnerability - a "liquidity scramble."
On that particular day, the cryptocurrency market witnessed an astounding opportunity, with over $12.8 million in arbitrage revenues up for grabs. To put this into perspective, the average daily arbitrage revenue typically hovers around $300K. Even when we exclude the most lucrative single arbitrage transaction executed by c0ffeebabe.eth, which raked in an impressive $5.4 million in revenue, the remaining arbitrage revenues still exceeded the average daily earnings, dwarfing even the sandwich attack revenues of $800K. This anomaly, compared to past observations, underscores the extraordinary scale of profits on that exceptional day.
The sudden massive arbitrage opportunity concentrated in attacked pools is illustrated in the treemap, which maps revenue distribution across 5,063 on-chain atomic arbitrage transactions that occurred on July 30th.
The treemap categorizes these transactions along two dimensions: bot address and whether the transaction was related to the Curve exploit. This results in three categories visualized:
attack-related transactions
Other transactions from attack-involved bots
Transactions from uninvolved bots
The treemap visually depicts the outsized proportion of revenues captured from the vulnerable Curve pools compared to other liquidity pools on that day. Attack-related arbitrage revenues stand out for their large rectangular areas, representing the sheer volume of profits up for grabs.
The liquidity scramble occurred as bots scrambled to capture these profitable opportunities before others could take advantage. There were 345 arbitrage transactions related to the four exploited Curve pools. Of 159 active arbitrage bots that day, 28 bots were involved in these exploit-related trades.
The analysis aims to uncover:
Given an opportunity like the Vyper exploit, how can arbitrage bots most swiftly and completely capture available profits?
What strategies should well-designed arbitrage bots implement to capitalize on such volatile conditions?
The report will distill key lessons around speed, efficiency, and tailored strategies by examining the behaviors and outcomes of the top trading bots active during the frenzy. Their competitive dynamics illustrate why these bots stand out in the MEV arena and showcase what it takes to maximize gains during market turmoil induced by unforeseen protocol vulnerabilities.
Specifically, the analysis to follow will showcase:
How these bots capitalized on brief bursts of profit
The clash between specialized bots employing different strategies
Using affinity analysis on transactions unveils bots' distinctive strategies
Here is a list of 8 key arbitrage bots during the frenzy, whose competitive tactics and strategies are dissected in the following parts.
Distinctive arbitrage bots
Bot 1:0x7d32C90762E22379235FC311fDB16fAB399Ed40A
Bot 2:0x0000000000a84D1a9B0063A910315C7fFA9Cd248
Bot 3:0xcb3702bc25B0F284b032e5edf1a1EbeA2FE43255
Bot 4:0xfd0000000100069ad1670066004306009b487ad7
Bot 5:0xBA3F5c056500cE033e9D74494B820D495efCF19d
Bot 6:0x0000000000007F150Bd6f54c40A34d7C3d5e9f56
Part 2 - Bots Pounce on Bursts of Profit
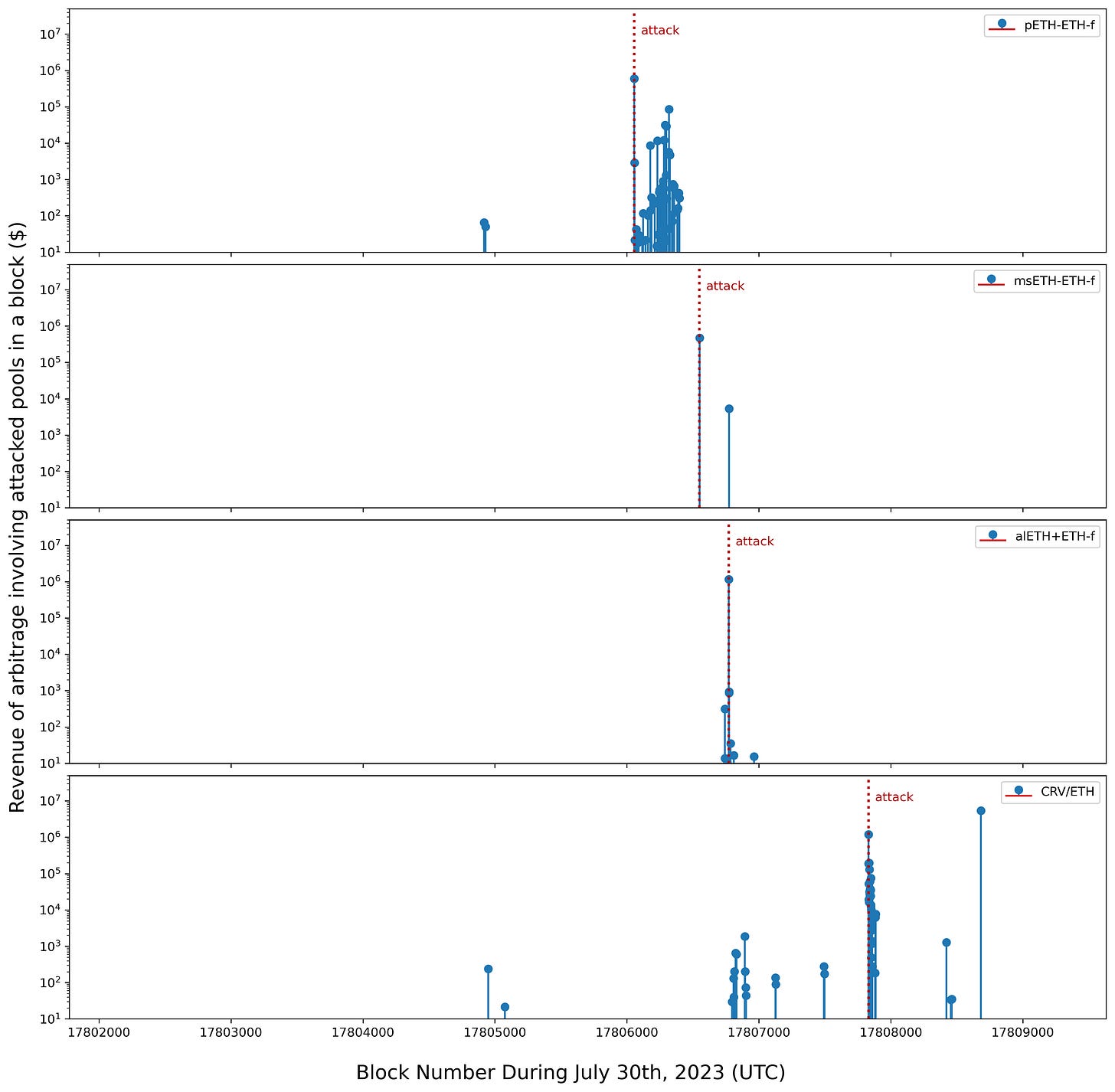
The two attached charts present the distribution of exploit-related arbitrage revenues across block numbers on July 30th using bubble and stem plots.
The bubble chart visually conveys how the most profitable trades clustered around the times of the Curve pool attacks. The stem graph pinpoints the occurrence time of the highest-revenue arbitrage transactions more precisely. Analysis of the data shows the fastest and highest-earning arbitrage transactions universally happened either in the same block as the attack transactions or the block directly after.
Time-series analysis reveals the enormous arbitrage profits that occurred in short bursts around the block times of the Vyper bug exploits on the Curve pools. Within these narrow windows, millions of revenues were realized repeatedly.
This extreme temporal concentration of profits implies bots must act within seconds to capitalize on the opportunities before others. Strategies focused on immediate execution were most successful in extracting value during the volatile spikes.
Additionally, a handful of isolated arbitrage transactions appear around block height 17805000 involving the pETH-ETH-f and CRV/ETH pools. Further exploration is needed on whether these are related to the subsequent attacks or arbitrages. If connected, they could represent early warning signs of the exploits.
Part 3 - Clash of the Liquidity Titans
In this part, we will spotlight four arbitrage bots involved in the pETH-ETH-f pool after the initial attack transaction:
Bot 1 - ⚡️ The Lightning Reflex Bot captured the first arbitrage opportunity after the attack, earning $296K profit after paying 50% of the revenue to the builder.
Bot 2 - 🐢 The Veteran Slow Bot performed arbitrage in this pool earlier that day, but missed the first post-attack opportunity.
Bot 3 - ⏩ The Follow-up Bot grabbed the second arbitrage in the pETH-ETH-f pool in the next block, netting only $427 after costs.
Bot 4 - 🦊 The Opportunistic Bot arbitraged related pools between Bot 1 and Bot 3's trades, profiting $1.5K after paying its builder $62K.
Bot 1: ⚡️ The Lightning Reflex Bot
Click here to view this arb done by Bot 1.
As shown in the figure above, Bot 1 captured the first post-exploit arbitrage opportunity through a standard triangular arbitrage transaction between pools: pETH-ETH-f, Vyper-contract, and SushiSwapPool.
Analysis of historical transactions from this bot's address shows it was an experienced arbitrageur regularly transacting across Curve, Uniswap, and SushiSwap.
Interestingly, closer inspection reveals Bot 1 performed two earlier Curve arbitrages on July 30th before this highlighted transaction. The first of these two aligns perfectly with the earliest outlier arbitrage transaction in the pETH-ETH-f pool at block 17804919 described in Part 2.
This provides evidence that Bot 1 was already active in these pools prior to the main attack. Its experience arbitraging Curve, combined with lightning-fast reaction time, allowed it to identify and capitalize on the initial post-exploit opportunity before any other bots.
The arbitrage performed by Bot 1 earlier in the day on July 30th has the same triangular path as Bot 1's winning transaction, but in the reverse direction. Notably, its Cost Revenue Ratio (CRR) was only 61% compared to most arbitrage bots, which pay over 95%.
Next, a natural question is - who performed another early outlier arbitrage in pETH-ETH-f described in Part 2?
It turns out it was Bot 2, executing the same triangular arbitrage as the winner, Bot 1. However, despite running the same path, Bot 2 failed to capitalize on the post-exploit opportunity.
Bot 2: 🐢 The Veteran Slow Bot
In fact, Bot 2 was a top-tier bot, consistently ranking in the top 10 for profitability, and capturing high-value arbitrage trades in two other exploited pools that day. But its 90%+ CRR indicates it lacked on-chain privileges.
Losing out to Bot 1's 50% CRR illustrates how priorities may confer competitive advantages. Further analysis of Bot 1's affiliated signal transactions reveals it relied on exclusive order channels and leveraged MEVBlocker's private order flows.
Notably, the original pETH-ETH-f attack transaction was actually a front-run transaction. Bot 1 could have discovered the opportunity either:
By detecting the front-run victim transaction in the mempool and back-run it
Through a private channel, tipped off about the front-run attack transaction first
Another difference is that Bot 2 often does not use Flash Loans. This can disadvantage capitalizing on large arbitrage spreads, as sufficient funds are required upfront. Had Bot 1 and Bot 2 competed on even ground via the first scenario, Bot 2's experience highlights the importance of deploying Flash Loans to seize on outsized opportunities.
Finally, Bot 2's denser historical transaction patterns across more protocols like Bancor also suggest potential limitations in managing capital and infrastructure across multiple pools simultaneously.
Bot 3: ⏩ The Follow-up Bot
The second arbitrage transaction in pETH-ETH-f after the attack occurred in the next block and was captured by a third bot, not Bot 1 or Bot 2.
This transaction performed the same triangular arbitrage path and direction as Bot 1. However, Bot 3 additionally conducted a 4-pool arbitrage to backrun its own triangular arbitrage in the same transaction.
At first glance, Bot 3's identical triangular path raises the question - did Bot 1 fail to capitalize fully, leaving arbitrage profits for Bot 3 to collect?
Bot 4: 🦊 The Opportunistic Bot
It turns out that in between these two transactions, Bot 4 inserted an arbitrage back-running Bot 1's transaction. Bot 4 could execute two backrun arbitrages against a SushiSwap pool in one transaction.
In comparison, while Bot 1 reacted fastest to capture the initial high-value post-exploit arbitrage, its ability to capitalize on successive opportunities appears less sophisticated.
For example, Bot 1 did not manage to incorporate the two follow-up backrun arbitrages by Bot 4 and Bot 3 into its own trade. Extracting the complete arbitrage value is an area for advanced bots to optimize, including capturing secondary opportunities and predicting the probability of successive signals.
The current leading technique is bundling back-run arbitrages on related pools - an initial engineering step towards capitalizing on secondary arbitrage chances.
A second improvement relates to priority management amidst an explosion of signals, like the ability to boost priority for the pETH-ETH-f pool in Bot 2's monitoring if it could predict further opportunities after its early arbitrage there. Better predictive tools to optimize signal management represent another competitive edge.
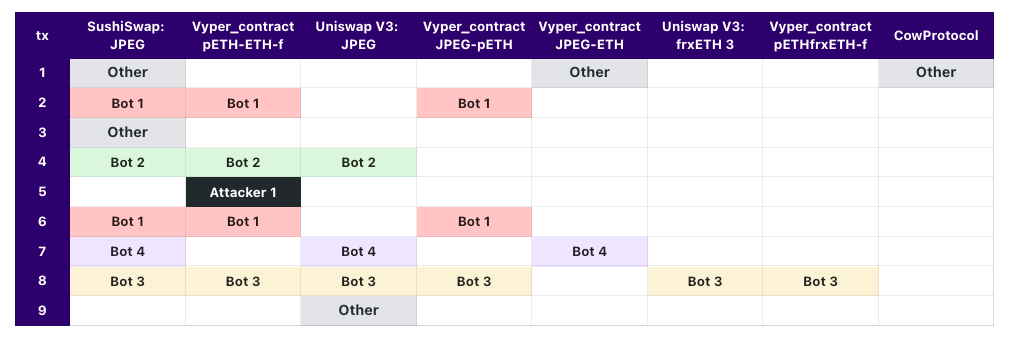
Transaction Affiliations
Visualizing and analyzing affiliated transactions in the following aggregated form can unlock deep insights into the competitive dynamics between arbitrage bots.
In summary, by dissecting these bots involved in highly correlated arbitrage transactions before and immediately after the attack, we can better understand the strategies and capabilities required to capitalize on volatile windows.
Part 4 - Affiliation Analysis Unlocks Deep Insights
To further demonstrate the power of analyzing transaction affiliations, Part 4 will examine activity after an attack on another Curve pool, alETH+ETH-f, on the same methodology.
The following affiliation chart makes the competitive dynamics between bots obvious through pool-linked transactions over time. By mapping the structure and sequencing of transactions, we gain deep insights into bot behaviors like back-running and sandwiches and chaining multiple profitable transactions together.
You can visit this shared spreadsheet to view the two tables above for details.
The Stood-Out Bot 5
In the chart above, tx 15 corresponds to the attack transaction at the Curve pool. Before the attack occurred, this pool was already a highly active trading area.
Although Bot 2 captured the first post-exploit arbitrage opportunity, Bot 5 stood out by back-running this trade and inserting nine subsequent arbitrages over the adjacent two blocks.
Remarkably, one of Bot 5's follow-on transactions even wiped out the remaining arbitrage value that Bot 2's original transaction failed to capitalize on fully (tx 21).
Despite that Bot 5 executed multiple arbitrage loops across different liquidity pools based on the same signal. Bot 5 also adopted a transaction-splitting strategy to improve its back-run success rate, e.g. Tx 22,23,24.
Similarly, in the fourth attacked pool CRV/ETH, Bot 2 again quickly captured the initial opportunity, but Bot 5 outperformed in finding additional transaction chances in the same block that Bot 2 missed.
The consistent use of PayloadDotDeZ6924798127 method reveals Bot 5 was a Payload builder's bot, explaining its ability to observe and back-run others' transactions. This highlights Bot 5's stronger advantage in discovery and executing multiple arbitrages per slot, demonstrating the benefits of a Searcher-Builder integration compared to a solo Searcher like Bot 2.
Other Bots
It's evident that in this arena, there are many other bots competing across composable pools. For example, Bot 6 represents the typical level of regular arbitrage bots, while Bot 4 again showcases outstanding ability in locating a long-tail arbitrage opportunity, finding it across six pools. Bots 7 and 8 can occasionally grab some opportunities. In one of the pools where these bots frequently trade, SwapFlashLoan, a transaction even became one of the four victims of the sandwich attack by a Sandwich Bot.
Summary
In summary, during periods of extreme market volatility, an increasing number of transactions become intricately intertwined. Bots find themselves needing to compose multiple pools to locate profitable opportunities and must adapt to swiftly track signals while employing various trading strategies to extract maximum value.
In this context, comprehending the intricate web of connections between transactions becomes paramount. The ability to analyze the affiliations between transactions poses significant challenges. These challenges underscore the complexity of navigating the cryptocurrency landscape during extreme market fluctuations.
As markets evolve, the symbiotic relationship between bots and market dynamics continues to reshape strategies and capabilities. Speed, precision, adaptability, and the ability to decipher transaction affiliations are becoming defining factors in the quest for profits and pinpointing problems in this dynamic environment.
This analysis showcases the value of diverse but tailored strategies, from rapid snipers to broad sweepers, in capitalizing on both large and small opportunities during volatile events. Tight coordination between searching for and executing arbitrage signals is key to maximizing profit. These findings provide guiding principles for arbitrage bot design and engineering as MEV capabilities continue advancing.