How Did A Malicious Validator Steal $20 Million From MEV Bots by Attacking Ethereum MEV Boost Relay
On Ethereum Block 16964664, the top 5 MEV bots on our leaderboard was exploited and lost $20M.
Around 2:11 AM EDT on April 3rd, the Twitter account punk3155 found some MEV bots had been attacked while trying to cook some sandwiches.
Interestingly, these 5 bots were in the top 10 MEV bots leaderboard of 30-day on EigenPhi.io.
The attack caused MEV searchers to face a chaotic situation because the attacker abused the assumed atomicity of the sandwich attack transaction bundle being sent to the chosen validator.
Usually, the typical process of block building involves sending a bundle through an API to builders, who then send all the block information to the relay. The relay transmits only the block header to the validator, adding the fee receipt address and parent of the block. Then the validator signs the relay's information before sending it to the consensus layer for broadcasting. However, during this attack, the validator attacker exploited a relay bug to access detailed transaction information that is not supposed to be visible to the validator until after the consensus layer has passed.
We just did a 2-min video analyzing the root cause of this morning's malicious validator event:
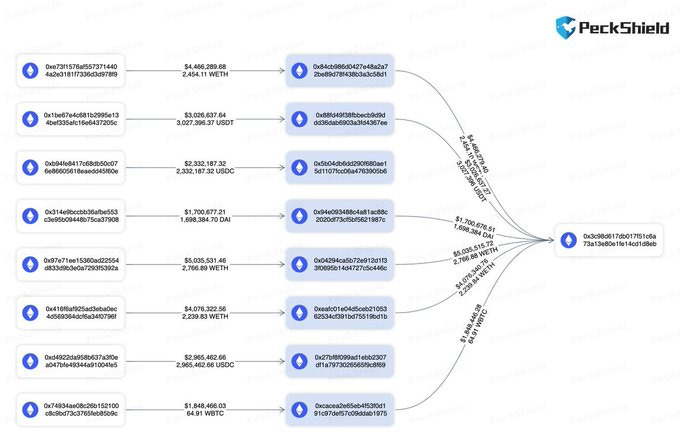
In block 16964664, which has 24 transactions, the attacker replaced the original victim's transaction with a new backrun targeting MEV bots, and the original backpiece of the MEV bot failed. The attacker transferred the profits to the address 0x3c98d, labeled as Sandwich the Ripper, currently holding $20 million in funds.
The validator 552061 of the targeted block 16964664 went offline after epoch 191813, and after the Shanghai upgrade, most of the validator's staked ETH can be withdrawn. The attacked MEV bots were the top earners in the sandwich bot game, and unfortunately, even the best sandwich chiefs became the appetizer on the table.
If you want to dig deeper, this mega thread by Shutter Network won’t disappoint you: