How Does the Grok Token Exploiter Exploit the X Token By Baking His Own Cake And Eating it?
A Deep Dive into the X Token Exploit to Unmask the Memecoin Manipulation

In the crypto industry, there are always people who won’t miss a chance to take a free ride. Last year, Elon Mask’s acquisition of Twitter gave birth to memecoins like Grok and X. While these tokens hoped to freeload degens, they became the target of someone more sophisticated.
Recently, we observed 2 arbitrage transactions utilizing the loophole of SPIKE token to generate a profit of $2.1K. The pattern of these 2 transactions is not new. A transaction that happened last June exhibits the same approach, whose victim is the X token. Let’s look at this transaction to understand the new way of exploiting memecoins.
N.B.: For the sake of clarity, different figure formats will be used below. But the serial numbers of the steps are the same.
One Liner
The bot utilizes the methods of the ERC20 X token to create the arbitrage opportunity between a Uniswap V2 pool and a Uniswap V3 pool, and takes advantage of it, making a profit of $4,844.
Big Picture
EigenTX Link: https://bit.ly/3xMOYIt
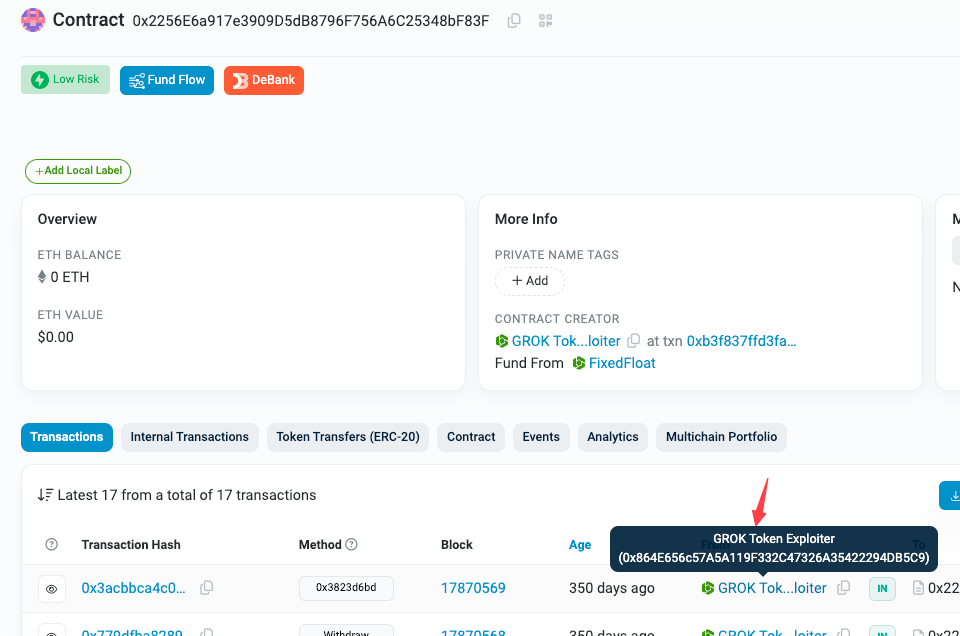
From the contract page on Etherscan, we can see the EOA labeled as GROK Toekn Exploiter did all the transactions.
Key Steps
Stage 1: Prep the Uniswap V2 X-WETH pool.
Step 0: Borrow 6,493,128,478.6032 X from the Uniswap V3 pool of X-WETH.
Steps 1-6: Swap 3,431,282,845.8058 X for 23.4081 ETH at UNI-V2, and transfer 34,659,422.6849 X back to X contract as a 1% tax.
Steps 7-12: Swap 34,312,828.4581 X for 0.2006 ETH at UNI-V2, transfer 346,594.2268 X back to X contract as a 1% tax.
Stage 2: Overflow the X contract to create the arbitrage prospect.
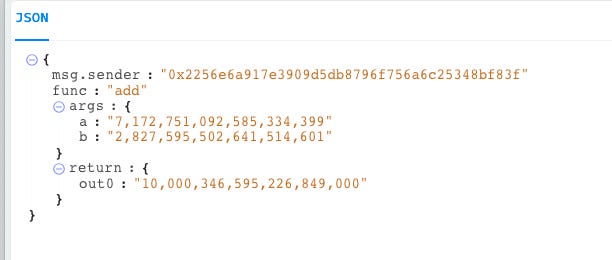
Step 13: Transfer 2,827,595,502.6415 X back to the X contract, bringing the balance of the X token of the X contract to 10,000,346,595.226849.
The simulation on Blocksec shows the effect.
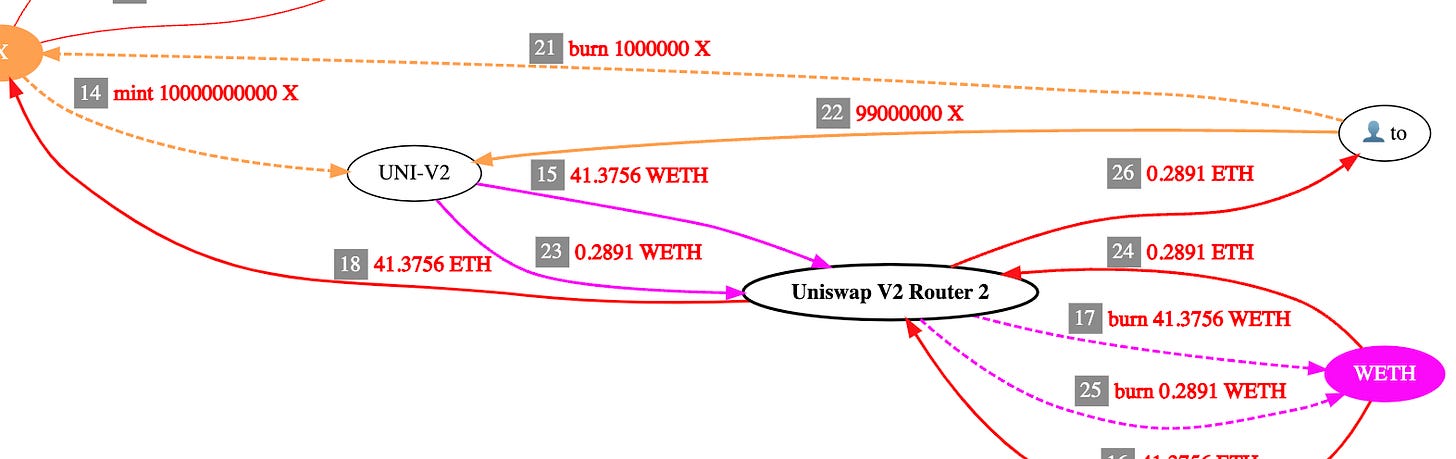
Steps 14-26: Swap 99,000,000 X for 0.2892 ETH at UNI-V2, and transfer 1,000,000 X back to X contract as a 1% tax.
The swapping of X for ETH this time triggers an internal function, X.shouldContractSwap(), returning true, which is the result of the code below:
aboveThreshold = balanceOf(address(this)) >= swapThreshold;The transfer in step 13 satisfies the condition: the balance of X is bigger than the threshold of 10,000,000,000. Before step 13, this code returns False.
You can find it in the contract of the X token.
Next, the X contract injects 10,000,000,000 X tokens into the Uniswap V2 pool and puts the received ETH to its deployer’s EOA.
This huge injection of X inflates its value, causing the exchange rate of X against ETH to surge to 342,323,651 X per ETH. The price gap between this Uniswap V2 pool of X-ETH and the Uniswap V3 pool of X-WETH.
We can split the steps of 14 to 26 as below.
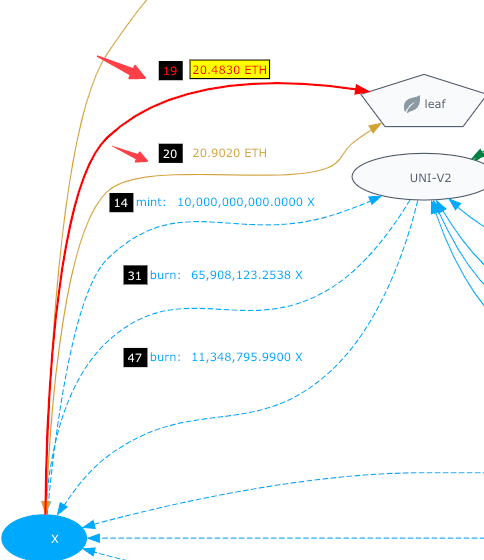
Steps 14-18: X contract transfer 10,000,000,000 X to UNI-V2 and swap X for 41.3756 WETH, unwrap WETH and transfer ETH back to X
Steps 19-20: X contract transfer 20.4830 ETH and 20.9020 ETH to an EOA address
Steps 21-26: To address finishes the swap operation at Uniswap V2 pool and pays tax.
Stage 3: Harness arbitrages.
Step 33: To address repays the flash loan, 6,558,059,763.3892 X, to the Uniswap V3 pool of X-WETH.
Steps 34-39: To address swaps 31,457,966.2838 X for 0.1402 ETH at the Uniswap V2 pool, transferring 317,757.2352 X back to X contract as a 1% tax.
Step 40: Borrow 5.1598 WETH from a new Uniswap V3 Pool of USDC-ETH.
Steps 41-48: To address swap 5.3 ETH for 1,123,530,803.0087 X at the Uniswap V2 pool, which transfers 11,348,795.99 X back to X contract as a 1% tax.
Steps 49-50: Swap 1,123,530,803.0087 X for 7.8274 WETH at the Uniswap V3 pool of X-WETH.
Step 51: To address repay the flashloan, 5.1624 WETH, to the second UniswapV3Pool.
Steps 52-53: Unwrap 2.6651 WETH to 2.6651 ETH.
Simplified Illustration
What about the SPIKE?
Using the SPIKE token’s internal functions to create a price gap between trading venues is exactly how a later bot does arbitrage.
Take this transaction, for example, showing the same pattern with a little divergence.
Stage 1: Preparing the Uniswap V2 pool of SPIKE-WETH.
Steps 0-3: Borrow SPIKE from the Uniswap V3 pool of SPIKE-WETH, swap for WETH in the Uniswap V2 pool of SPIKE-WETH.
Stage 2: Overflow the SPIKE contract to create the arbitrage prospect.
Steps 4-10: Overflow the SPIKE contract to mint 4,206,900,000 SPIKE and inject them into the Uniswap V2 pool of SPIKE-WETH, creating the arbitrage opportunity. Here is the difference. This prospect is not between the Uni V2 pool and Uni V3 pool. Instead, it’s between the old exchange rate and the new one in the same Uniswap V2 pool of SPIKE-WETH.
Stage 3: Harness arbitrage.
Steps 11-19: Swap the left SPIKE for WETH and return the loan to the Uniswap V3 pool of SPIKE-WETH, taking a profit of $1.2K
Conclusion
The X token exploit showcases a clever way of gaming the memecoin market. These arbitrage bots can rake in substantial profits by manipulating the token's internal functions and creating price gaps between different trading venues. The Grok Exploiter follows a similar playbook, with slight variations in execution.
These incidents serve as a reminder that in the world of memecoins, especially those riding on the coattails of tech billionaires or trending topics, there's always someone looking to outsmart the system. While some might see these tokens as a quick path to riches, others view them as prime targets for exploitation.
As the crypto landscape evolves, so do the tactics of those seeking to exploit it. Whether you're a developer, investor, or just a curious onlooker, staying informed about these mechanisms can help you navigate the often turbulent waters of the cryptocurrency world.
Want to learn more about the DeFi lego? Visit our Head First of DeFi to decode the DNA of DeFi Transactions & Strategies.
Follow us via these to dig more hidden wisdom of DeFi:
EigenTx | Website | Discord | Twitter | YouTube | Substack | Medium | Telegram