EigenTx Use Cases for Beginners: $3.2M Arbitrage, Its Back-Run, MEV Redistribution, and Jaredfromsubway.eth Sandwich
Demystifying The Lego of Decentralized Finance: How EigenTx Brings Transparency and Efficiency to On-Chain Transactions
Blockchain technology makes financial transactions transparent and trustless. Understanding blockchain asset movement helps protocols improve product design and identify and mitigate risks. However, the composability of Smart Contact makes data analysts and regulators struggle to analyze blockchain transactions.
No worries! We are excited to introduce EigenTx, which can help data analysts, researchers, regulators, and traders find alpha in the fast-changing DeFi market by revealing truths and trends. EigenTx lets users analyze complex smart contracts and unstandardized token functions. EigenTx also aims to improve financial industry efficiency and innovation by improving on-chain transaction transparency and insights.
In this article, we will use four actual transaction examples for beginners, including Simple Arbitrage, Back-Run, MEV Redistribution Using MEVBlocker, and Jaredfromsubway.eth, to streamline your engaging with the DeFi world.
Download our booklet to see more cases in advance: EigenTx: Examining the Lifecycle of Token Flows-A Guide to Analyzing Complex Transactions
Case 1. 2022’s Most Lucrative Simple Arbitrage: $3.2M Profit
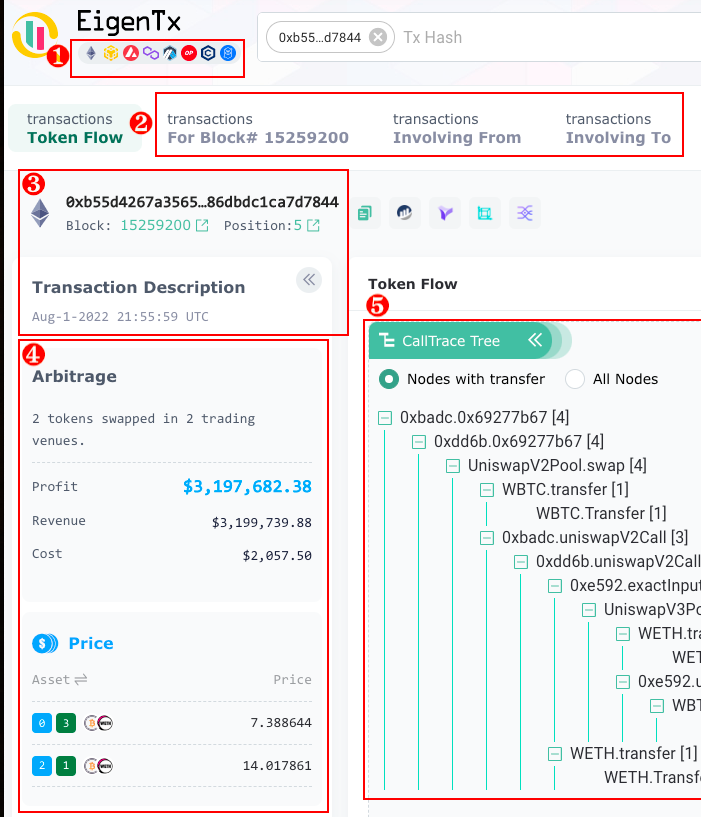
This simple atomic is the most profitable MEV of 2022. We use it to show EigenTx's basic features in the image below. In the lower right, ellipsoids represent addresses, arrows represent amounts and transfer directions, and symbols represent token flows. Thus, in four steps, one can find the "to" address earned 1,967 WETH as revenue!
This page also shows information other than the token flow chart:
EigenTx supports multiple chains, including Ethereum, BSC, Avalanche, Polygon, Arbitrum, Optimism, Cronos, and Fantom.
Links to the pages displaying related transactions from the same block or involving either the same “from” or “to” addresses.
Basic information about the transaction.
MEV type detected by EigenPhi, the transaction’s PnL, and swapping prices.
CallTrace Tree that links to the token flow chart step by step.
Link to view in one chart if you are searching for multiple transactions
Alert for risky contracts
Settings for higher-tier options that can further consolidate the token flow chart
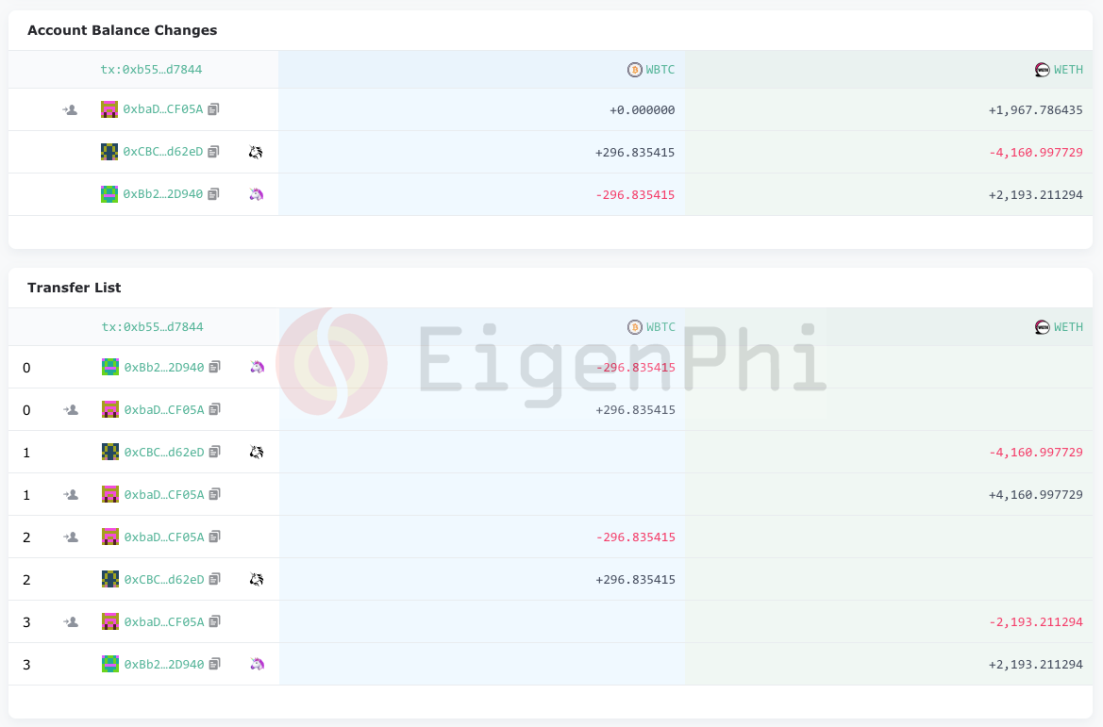
The Account Balance Changes and Transfer List displays balance variances of participants and transfers among them to help users understand the transaction with exact amounts.
Case 2. Back-run Transaction
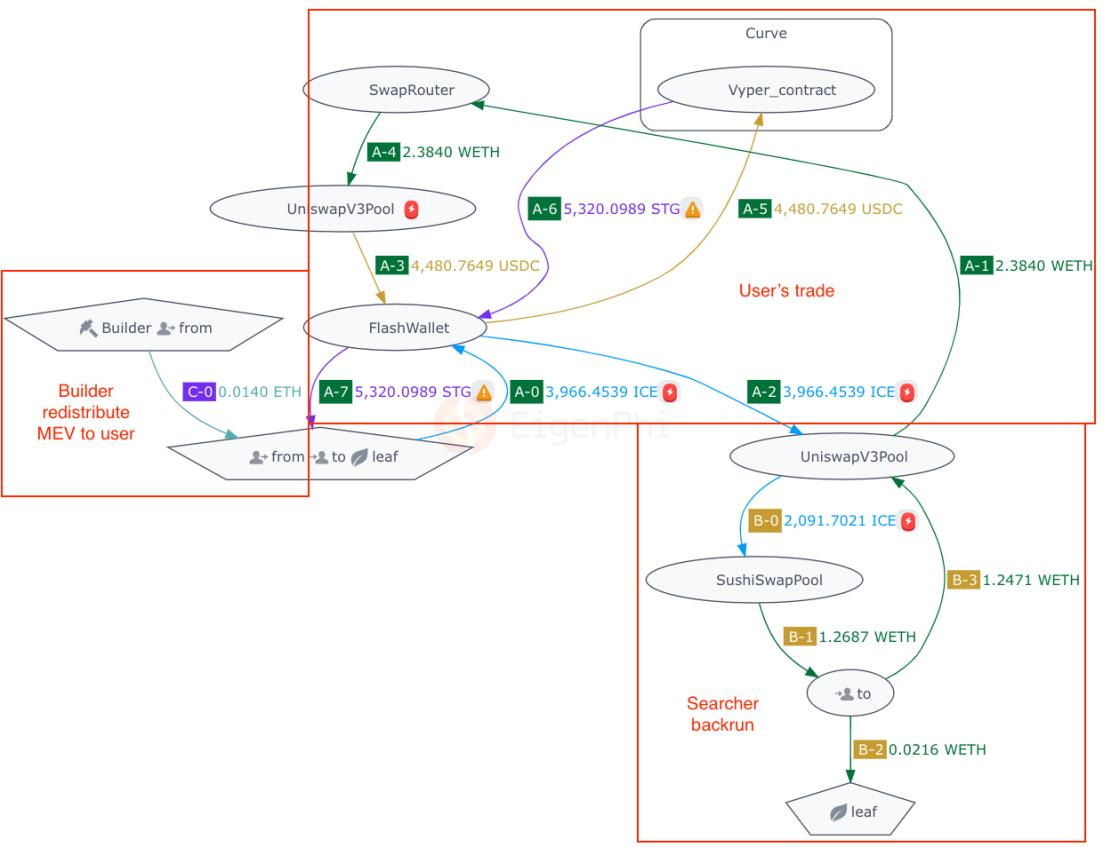
Where does the most profitable arbitrage opportunity originate from? We found three related transactions numbered 3, 5, and 6 in block height 1525920 on the related transaction page. Transaction 3 exploited Nomad to cash out 300 WBTC, causing UniswapV2Pool's WBTC/WETH price to fluctuate. We’ve analyzed transaction 5 as case 1. The same arbitrage contract executed transaction 6 as the secondary back-run arbitrage.
We can graph these three transactions into a single image to give you a bird's-eye view.
Steps A-0 through A-6 show the Nomad exploit.
Steps B-0 through B-3 and C-0 through C-3 show two arbitrage transactions retracing the previous transaction.
Case 3. MEV Redistribution Using MEVBlocker
Do you know MEV Blocker can protect you from most frontrunning and sandwich attacks on all types of transactions? In addition, searchers will refund 90% of the profit of back-running transactions to the traders. But how does it work exactly?
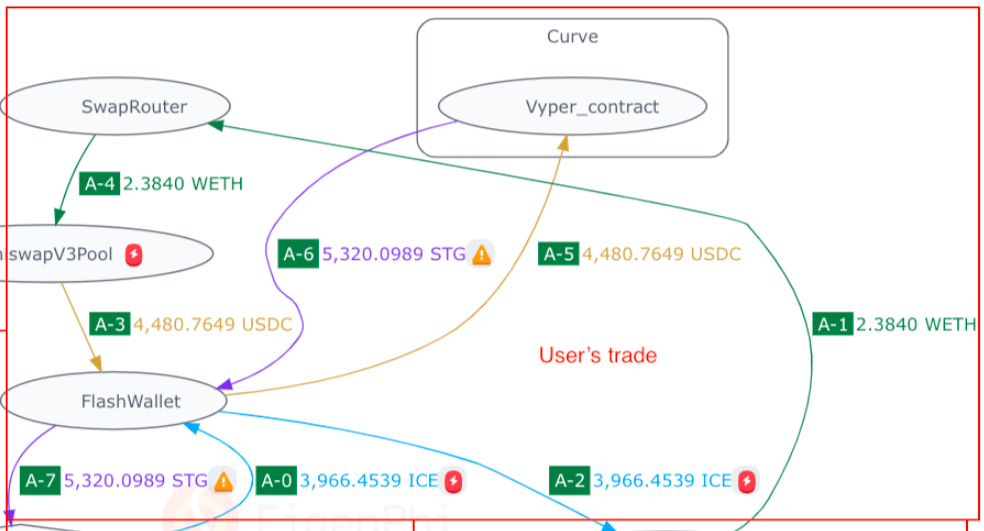
We have a set of transactions from the MEVBlocker service at block height 16993297. This token flow chart combines three transactions.
User trades ICE for STG in A-0 to A-7.
The searcher back-runs the first trade at a UniswapV3Pool.
Builder0x69 built this block and returned some MEV to the user in the third transaction. This completes MEV redistribution.
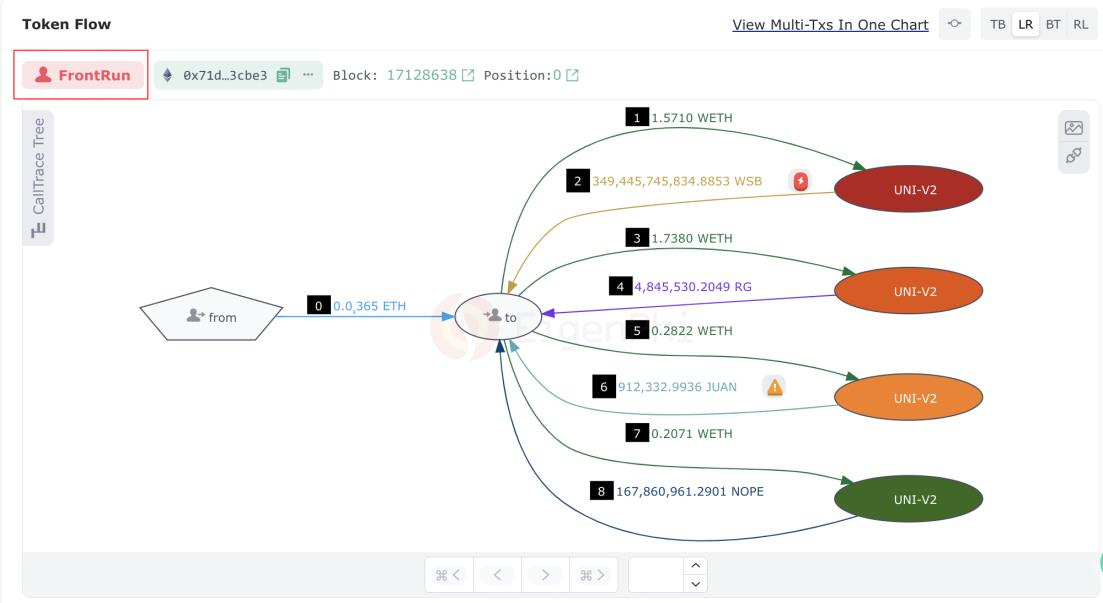
Case 4. JaredfromSubway's hybrid sandwich trading
As stated in our previous analysis, jaredfromsubway.eth's trading strategies are distributed across numerous transactions, making it difficult to see the big picture. The bot uses sandwich attacks, including conventional front-running and back-running. This famous sandwich bot's diverse trading strategies can be easily examined with EigenTx.
EigenTx lets users search for multiple transactions of sandwich attackers' front-running, victim transactions, and back-running. Enter the hashes of these transactions, separated by commas, into the search box, and EigenTx will show the results.
A typical sandwich attack executed by this bot as an illustrative example.
Four UNI-V2 pools were swapped in this sandwich attack's front-running phase. WETH was traded for WSB, RG, JUAN, and NOPE.
Five victims were attacked in the same block for similar exchanges.
Finally, the attacker converted tokens to ETH during back-running.
EigenTx's features facilitate the analysis of these transactions:
Users can input multiple transactions in the search box, separated by commas.
Each transaction will be labeled with its corresponding role in the sandwich attack: front run, victim, or back run.
The attacked pool will be highlighted using the same color between the attacker's Txs and the victim's Txs for easy identification and analysis.
"Transactions Involving To" can identify this bot's transactions. EigenPhi labels transactions near the searched transaction sandwich attacks, as shown below. This feature lets users understand the bot's transaction patterns and behavior.
Continue following for more examples of MEV cases! In the meantime, follow us and get our latest booklet for free by clicking here.
Follow us via these to dig more hidden wisdom of DeFi:
Website | Discord | Twitter | YouTube | Substack | Medium | Telegram