The best way to avoid becoming a victim of the Sandwich attack is to learn how it works.
A complete Sandwich attack involves "sandwiching" the transactions between two transactions initiated by the searchers. Here we will unpack a typical Sandwich attack that takes advantage of the AAVE's loan. Let's start.
Stakeholders
Address
MEV 🤖: 0xe8c060f8052e07423f71d445277c61ac5138a2e5 ("to" in the Figure 1&4)
Contract: 0x5423a31ecdc46ac59a863c920446e410449e39e4 ("0x5423" in the Figure 1&4, possibly an MEV 🤖)
Victim: 0x0fad8bcb3d9f9e1dd4de342a1971e2cc8c79e870 (Not shown in the figures)
Protocol
AAVE V2 Collector: a decentralized non-custodial liquidity markets protocol where users can participate as depositors or borrowers. In AAVE Protocol V2, debt positions are tokenized, so borrowers will receive tokens that represent their debt.
Uniswap V3: a protocol that allows for direct peer-to-peer cryptocurrency transactions to take place online without the use of an intermediary.
Tokens
aTokens: tokens minted and burnt upon supply and withdraw of assets to an Aave market. More details can be found at Aave's documentation.
aUSDC: AAVE $USDC
aWETH: AAVE $WETH
variableDebtWETH: Tokens that represent the debt of $WETH on AAVE V2
Fee
Miner tips: The fee is paid to cryptocurrency miners, which performs the work to verify the next block of transactions added to the blockchain.
Gas fee: The blockchain networks often charge a fee for their validators, and the fee is required to conduct a transaction successfully.
How it works
The First Transaction by the Attacker
Keep waiting until an innocent target appears. After detecting the victim's intent to swap $WETH for $USDC, all the attacker needs to do is to increase the exchange rate of $WETH regarding $USDC, meaning the user would get fewer $USDC with the same amount of $WETH, comparing the transaction without the attack.
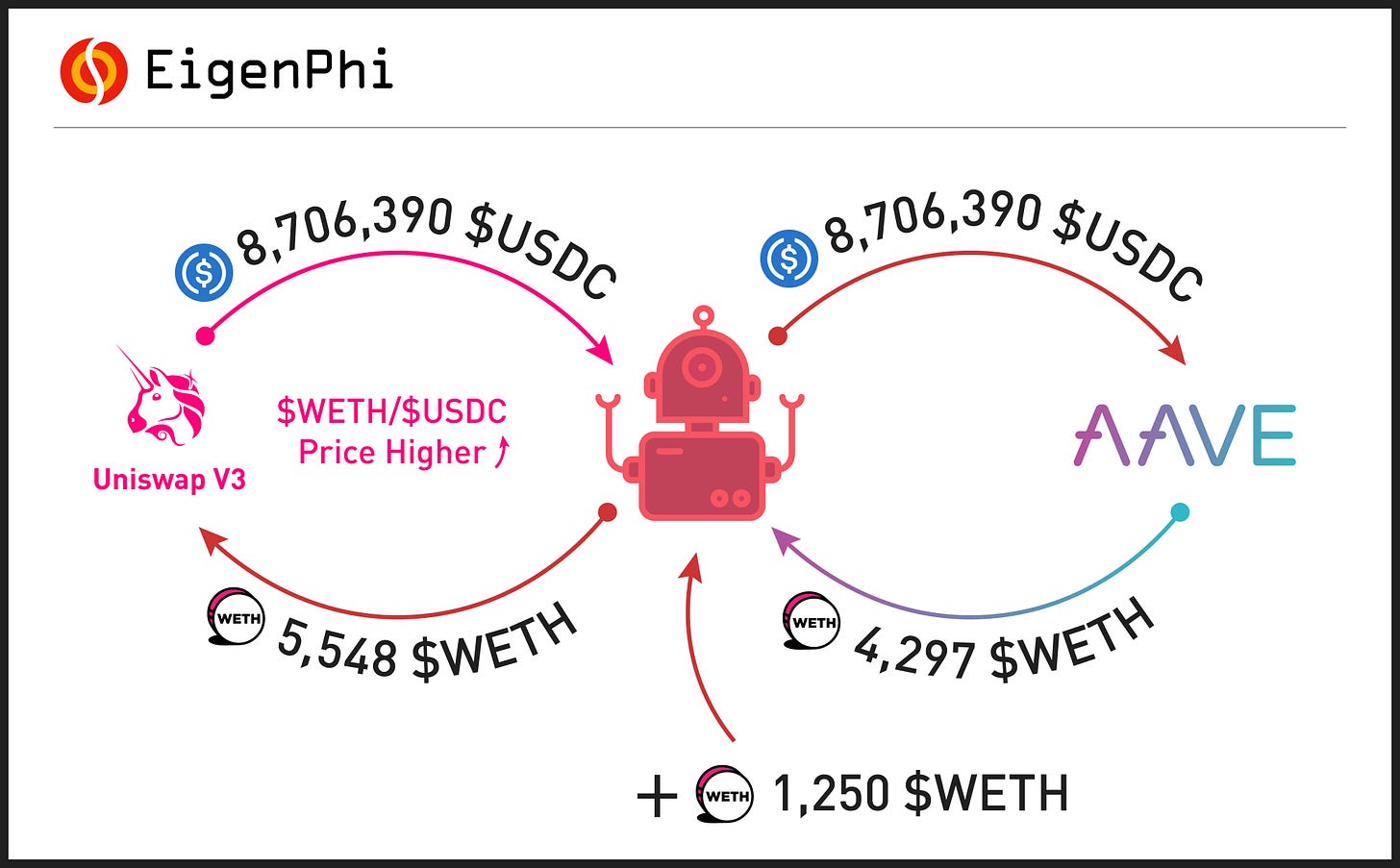
As shown in Figure 1:
The #MEV 🤖 transferred 1250 $WETH to the contract 0x5423 (Step 0), and got $8,706,390 $USDC from the Uniswap V3 pool (Step 1).
Following the contract, the MEV 🤖 deposited the $8,706,390 $USDC got from Uniswap V3 at AAVE V2 (Step 3,4), which allowed users to "swap their deposited assets, even the ones being used as collateral, to another asset". The gas fee was 1.1364 $aUSDC (Step 2).
Subsequently, the MEV 🤖 was able to take out 4,297 $WETH in return, with a 0.0153 $aWETH gas fee (Step 5,7). Additionally, 4,297 $variableDebtWETH were minted to record the debt (Step 6).
Finally, the borrowed 4,297 $WETH, as well as the initial capital - 1,250 $WETH, was returned to Uniswap V3 (Step 8).
Highlight
Attention: Though the procedures were presented in a logical order, all steps were finished in a single, atomic transaction.
Initially, 8,706,390 $USDC was used as collateral to borrow 4,297 $WETH, as the MEV 🤖 did on AAVE V2 (see Figure 2).
With another 1,250 $WETH, the overall 5,548 $WETH returned to Uniswap V3 had lowered the $WETH/$USDC price, which meant 1 $WETH swaps fewer $USDC.
The whole process served as a swap for 8,706,390 $USDC with 5,548 $WETH on Uniswap V3, while 4,297 $WETH was borrowed from AAVE V2. After the swap, 5,548 $WETH were needed to buy 8,706,390 $USDC.
The Second Transaction by the Victim
Then, when the victim wanted to swap 1,037 $WETH for $USDC (see Figure 3), the guy had to buy $USDC at a lower $WETH/$USDC price. The victim got 1,603,498 $USDC in return, but it should have got more than that. The part squeezed by the Sandwich attack was the victim's loss, but also the MEV 🤖's revenue.
The Third Transaction by the Attacker
As part of the whole attack, MEV 🤖 should make a reversed transaction of the initial one to win its revenue back (see Figure 4).
The MEV 🤖 completed reversed transaction as the following:
The MEV 🤖 got $5,572 $WETH from the Uniswap V3 pool (Step 1) and returned 4,297 $WETH to AAVE V2 (Step 3).
Thus, the corresponding 4,297 $variableDebtWETH was burned (Step 2)the MEV 🤖 was able to retrieve its once deposited 8,706,390 $USDC from AAVE V2 (Step 4,5).
In the next step, the MEV 🤖 paid 8,706,390 $USDC back to Uniswap V3 (Step 6).
In the end, MEV 🤖 got 1,275 $WETH (Step 7). Its total revenue was then (1,275-1,250) $WETH, namely about 25 $WETH.
To make sure that the full three transactions can be successfully acknowledged, MEV 🤖 generously paid about 14.5881 $ETH to the miner (Step 8,9,10) and recorded them in block 15266509.
Summary
Let's take a quick look at the Profit & Loss Statement (see Figure 6). Overall, this Sandwich attack brought the attacker over 24.3378 $WETH in revenue.
After paying the gas fee (1.1364 $aUSDC & 0.0153 $aWETH) and the miner tips (14.58 $ETH), the MEV 🤖 has earned a profit of over 9.7254 $WETH, or $15,577.
Okay. That's all for this outlandish Sandwich. This is never the end, but a new start to your journey inside the MEV world.
Please follow us to keep updated with frontrunning, and please let me know if you are interested in the tool that generated the flow charts above.
Follow us via these to dig more hidden wisdom of DeFi: