Attacking User Adding Liquidity, This Sandwich ripped off $870K from the Victim
And another arbitrage bot made $44.5K profit out of the ripple effect.
On Jan-20-2025 05:03:11 AM UTC, a sandwich MEV became one of the biggest sandwich MEV attacks for a long time. The preyed user was deprived 9.95 wBTC, worth $870K while adding liquidities to a Uniswap V2 pool, only lost almost all of them.
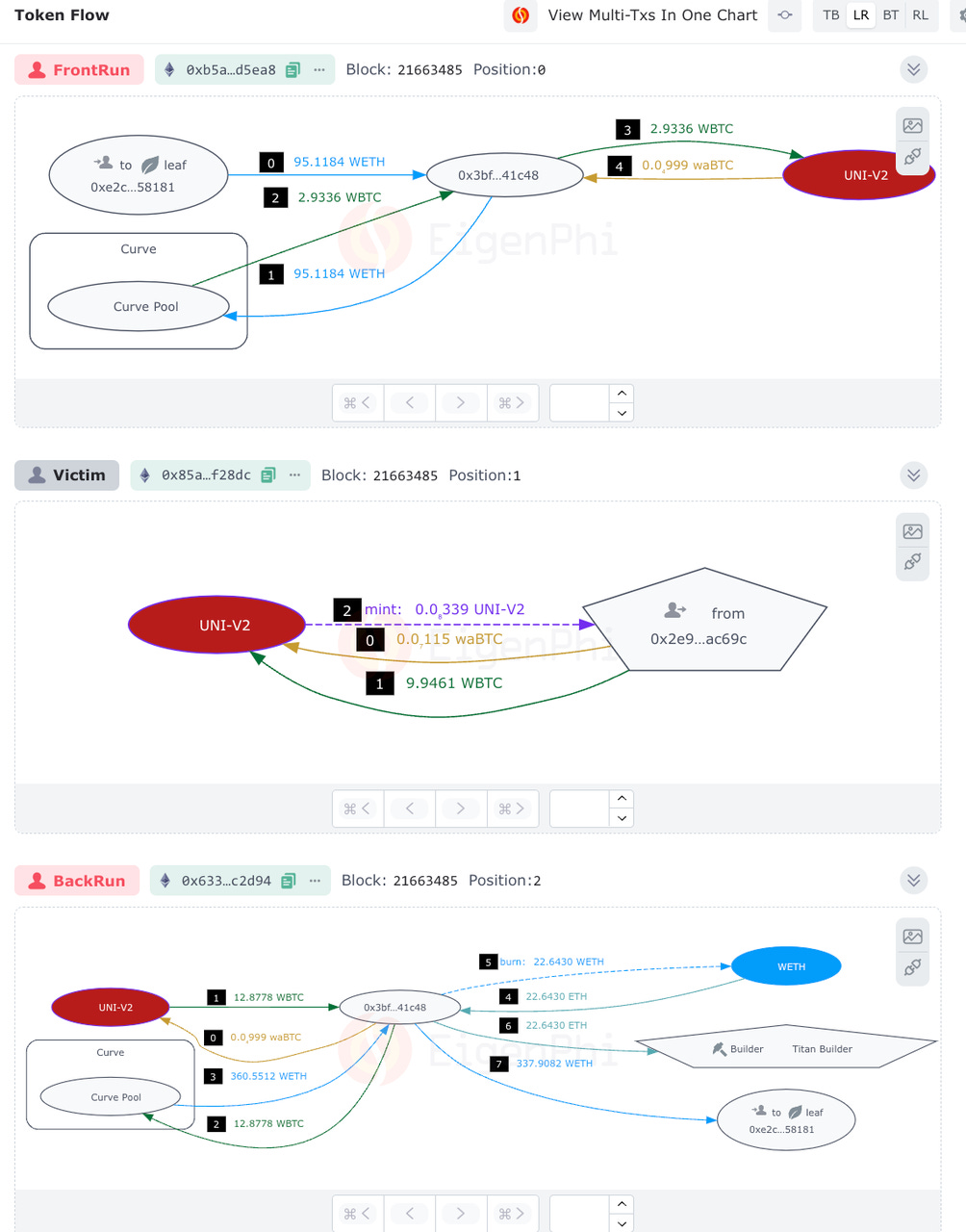
This is the token flow chart of the attack.
How Did It Happen?
The Uniswap V2 pool had severely low liquidity, which could be the reason triggering the user’s intention to add some.
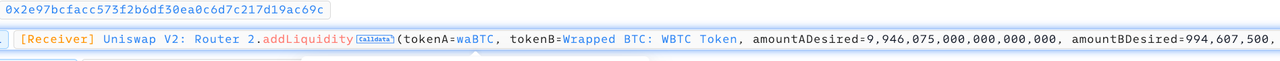
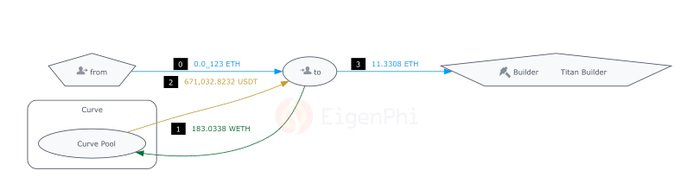
Originally, the user aimed to add 9.946 WBTC and 9.946 waBTC simultaneously, which can be seen via the Invocation Flow of BlockSec’s Phalcon tool.
Sadly, the user sent their intent to the public mempool, where malicious actors lurk. In this case, sandwich bot 0xe2cd.
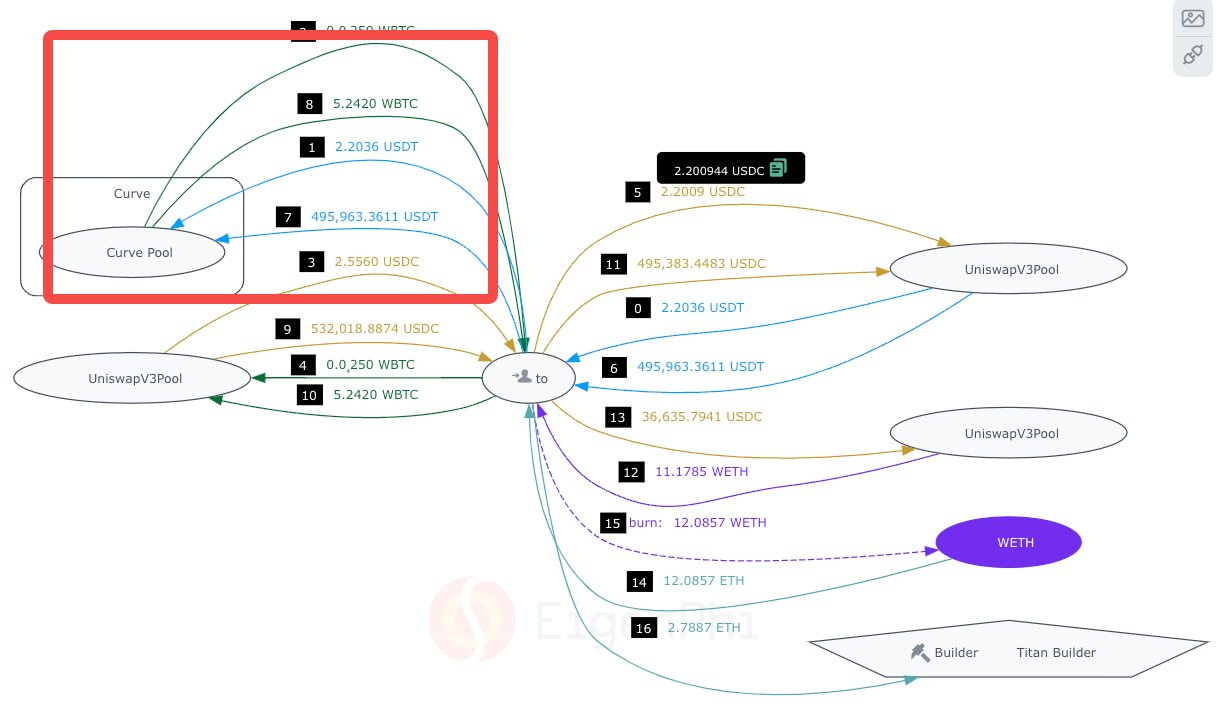
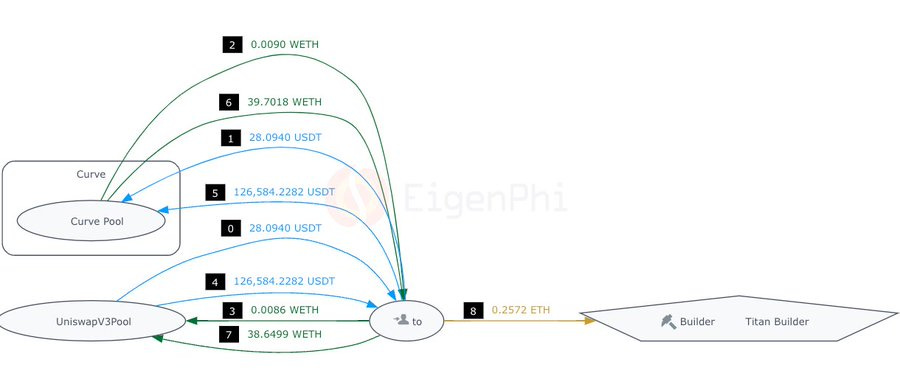
Detecting the user’s adding liquidity operation, the bot swapped 95.1184 ETH to 2.9336 WBTC via the Curve pool and sent the 2.9336 WBTC to the Uniswap V2 pool, pumping the exchange rate of waBTC against WBTC extremely high. This is the Front Run in the image above.
The manipulated price in the pool impacted the user’s operation. Since they did not set a critical parameter, AmountAMin, which we will talk about later, the accepted liquidities were 9.9461 WBTC, and a very small amount of waBTC. This process is shown in the figure as the victim transaction.
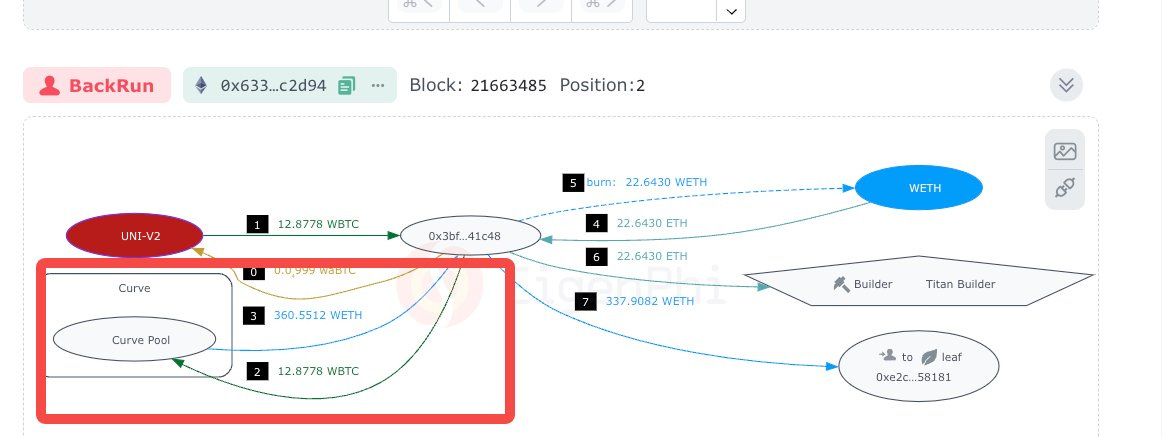
After the victim transaction, the bot immediately inserted another transaction, the Back Run transaction, in the figure, emptying the Uniswap V2 pool by swapping a negligible amount of waBTC for 12.8778 WBTC, including the 2.9336 WBTC they put into originally, out due to the unchanged and still extremely high rate. Then the bot exchanged the WBTC to more than 360 ETH, tipped the Titan Builder 22.6 ETH, and took 337.9 ETH away.
How to Avoid Such Miserable Scenarios?
In retrospect, the victim could have done 2 things differently.
Use an RPC that prevents frontrunning.
MEV-Share and MEV Blocker are two obvious choices. These PRCs would prevent your orders from being exposed to perpetrators. And you may get a refund for using them because of the arbitrage opportunities your trade creates.
Set the amountAmin parameter.
When adding liquidity to a pool, always set a minimum acceptable value (amountAmin), the minimum amount of tokens you are willing to accept when adding liquidity.
This parameter acts as a transaction safety mechanism. If price manipulation causes the actual token amount to fall below this set minimum, the transaction reverts.
Here is how it works:
Normal pricing conditions allow for expected token amounts to be added.
Significantly lower actual amounts indicate price deviation from normal levels.
Transaction reversion prevents liquidity addition at unfair prices.
This mechanism functions like slippage protection. When amountAmin is set, it safeguards against malicious price manipulation.
In essence, amountAmin acts as a threshold checker: if the added liquidity falls below this value, it signals incorrect pricing and prevents the transaction.
Any Ripple Effect?
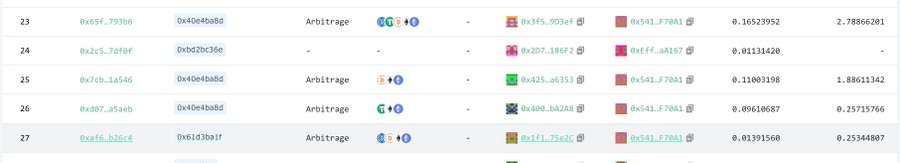
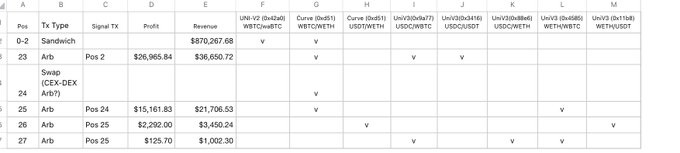
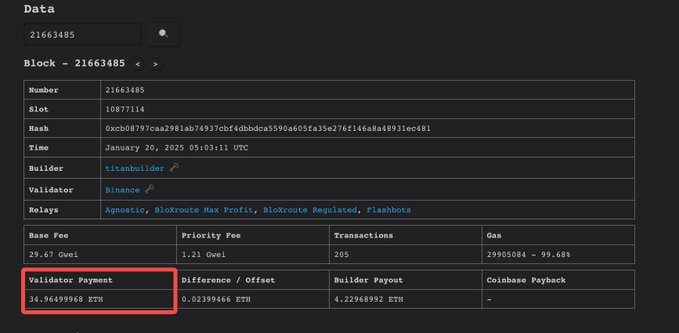
Exploring block 21663485, which includes this Sandwich at the top, we discovered that four more arbitrages, by bot 0x5413, and possibly one CEX-DEX arbitrage, by bot 0xEff6, benefited from the attack.
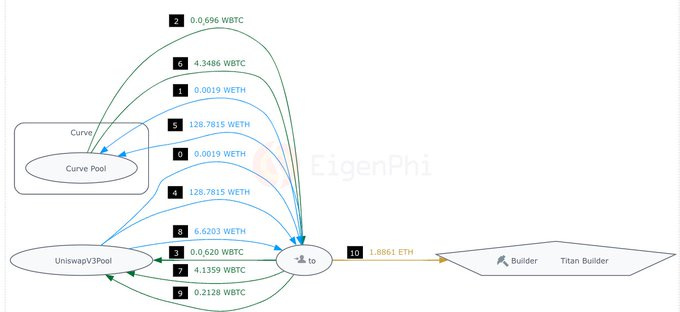
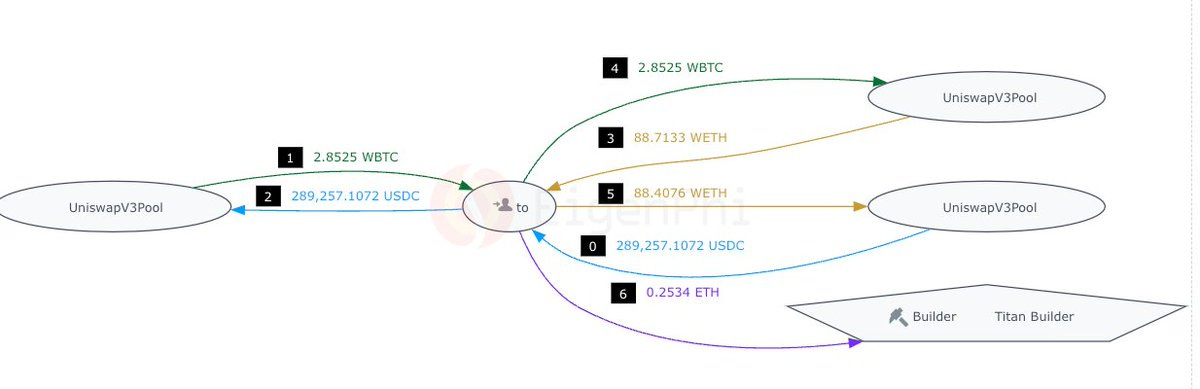
On Pos 23, bot 0x5413 took advantage of the price discrepancy created by the backrun in the curve pool and made a $ 27k profit-arbitrage by bribing Titan Builder 2.8 ETH.
The transaction on Pos 24 appears to be an innocent swap at first sight. Looking harder, you can see that bot 0xEff6 uses the same pool for the exchange while bribing 11.3 ETH to the builder to get this position in the block. Who would have done that for just a swap?
Open the Etherscan page of bot 0xEff6; it's obviously a high-frequency trader. And we can't identify any atomic MEVs it has done.
Considering the generous tips it gave the builder, 🤖 0xEff6 was definitely doing something else on CEX to cash out this opportunity.
On Pos 25, bot 0x5413 uses the CEX-DEX arb transaction as a signal to finish an arbitrage between the Curve pool and the UniV3 pool, tipping Titan 1.9 ETH.
Two transactions on Pos 26 and 27 receive less profit, inheriting the impact of the previous arbitrages.
This table shows the relationship between these MEVs and the pools they use.
The Sandwich bot reigns supreme, raking in a jaw-dropping $796K profit. Hot on its heels is the lucky block proposer, pocketing 35 ETH ($112K) from Titan Builder, as featured on payload.de.
Meanwhile, Arb bot 0x5413 scored $44.5K through four savvy trades. The P/L of the CEX-DEX bot 0xEff6 remains a mystery.
In summary, this is a perfect case showing that a single MEV opportunity often unfolds as an intricate dance of multiple transactions involving numerous participants competing and collaborating across different protocols.
Always Use Protection with Caution
This devastating $870K loss serves as a stark reminder that MEV attacks remain a serious threat in DeFi, with this single attack triggering a cascade of subsequent arbitrage opportunities worth over $840K in total profits for various bots. Users can protect themselves by implementing two critical safeguards: utilizing anti-frontrunning RPCs like MEV-Share or MEV Blocker, and always setting appropriate amountAmin parameters when adding liquidity. These simple yet crucial steps can mean the difference between a successful transaction and catastrophic losses. Don't let your assets become another cautionary tale.
You can also click this link or open https://bit.ly/hfdefi to download the free ebook Head First DeFi, Decoding the DNA of Crypto Transactions & Strategies.
Follow us via these to dig more hidden wisdom of DeFi:
EigenTx | Website | Discord | Twitter | YouTube | Substack | Medium | Telegram