$6.9M Lodestar Exploit: Oracle Manipulations Through Attacking Issuance Mechanism Vulnerabilities
And how to use right tools to identify the gains and losses of all parties involved.
Several recent incidents have revealed vulnerabilities related to specific tokens' issuance mechanisms and manipulation attacks on oracles. These incidents include, but are not limited to, the Ankr private key breach & Helio exploit (BSC), Lodestar exploit (Arbitrum), dForce exploit (Arbitrum & Optimism), and Platypus (Avalanche). We previously analyzed the Ankr incident and the implicated lending protocol, Helio, which created arbitrage opportunities for MEV searchers. In this series of articles, we will explore the attack principles of the other three incidents and incorporate them into discussing the previously proposed analysis framework, The Tokenomic Trilemma. This analysis will shed light on the topic of oracle manipulations.
Moreover, our analysis will demonstrate how the token flow chart of EigenTx can help us accurately identify the gains and losses of all parties involved, providing a more precise basis for determining compensation and accountability.
The Exploit: A Tale of Cross-Protocol Theft and Oracle Manipulation
On December 10th, 2022, an attacker known as 0xc29d, successfully sent a transaction targeting Lodestar Finance on Arbitrum and transferred the proceeds to the Ethereum main net through cross-chain protocols within minutes. More than four hours later, @SolidityFinance tweeted and pointed out the vulnerability in the composability of Lodestar's oracle and PlutusDAO's donate function. @LodestarFinance also tweeted their protocol was attacked, and paused the market, stating that the attacker manipulated the exchange rate between plvGLP and GLP.
CoinTelegraph compared this incident to the Mango Squeeze, but it is not as simple. The Mango Squeeze attacker, @avi_eisen's team, manipulated the market price to achieve excess borrowing by taking advantage of the low liquidity of the collateral’s underlying token. The Lodestar attacker found a vulnerability in the issuance mechanism of plvGLP and manipulated the oracle based on the altered information.
On December 27th, 2022, the U.S. Attorney’s Office charged Avraham Eisenberg, who had publicly claimed to have conducted the Mango squeeze event, with market manipulation and arrested him. However, the Lodestar attacker remains mysterious and fled with the funds.
Primary Attack Transaction
The chart above illustrates the primary asset flow of the incident, which involved three protocols deployed on Arbitrum: Lodestar, GMX, and PlutusDAO.
Lodestar is an over-collateralized lending protocol that forked Compound, the biggest victim of this attack. The risk involved their self-built oracle, GLPOracle, which evaluated the plvGLP collateral value in the lplvGLP lending pool.
GMX is a decentralized perpetual contract trading platform that provides long, short, and swap functions. It issues governance tokens GMX and liquidity tokens GLP, obtained by pledging assets.
PlutusDAO is an incentive governance protocol built on top of other protocols. For example, GLP token holders can stake GLP on the platform to obtain plvGLP and additional rewards. plvGLP holders can further stake their tokens to receive plsGLP.
Lodestar opened a lending pool for plvGLP, and users can deposit plvGLP to borrow other assets and vice versa. The available LTV set for plvGLP in the protocol is as high as 0.8.
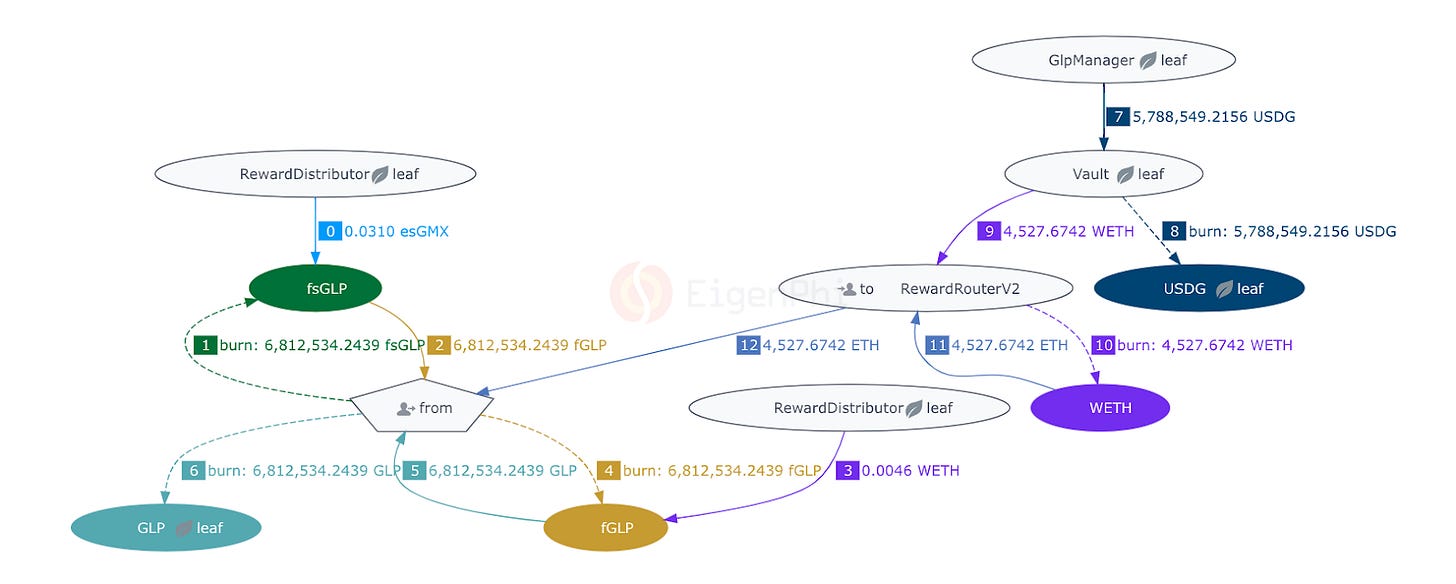
You can regard plvGLP as the share token of the GLP staking pool. The attacker called the function donate() of PlutusDAO's plvGLP Depositor contract to stake GLP assets to the plvGLP contract without issuing new plvGLP tokens. This action caused the AUM value of the contract to increase without changing the number of corresponding plvGLP tokens issued.
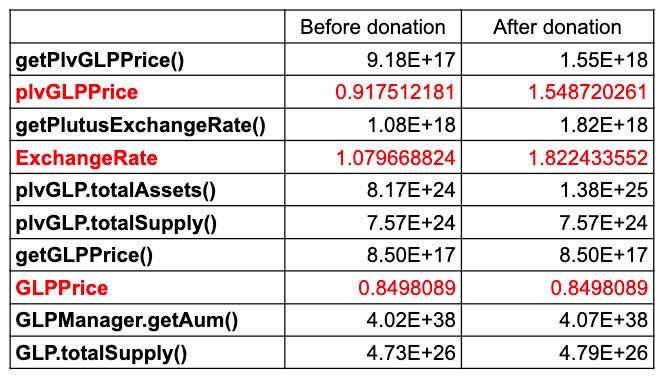
This trick triggered a severe error in calculating the exchange rate between plvGLP and GLP by GLPOracle (overestimation of about 1.8 times), raising the valuation of plvGLP.
Using this, the attacker deposited $70.1M obtained through flash loans to Lodestar, borrowed plvGLP close to the LTV limit, and cycled it back to Lodestar.
The attacker then borrowed $2.36M through flash loans again, deposited most of the funds (including 1580 WETH of self-owned funds) to GMX's Vault contract to obtain GLP, and manipulated the net asset value and share of the plvGLP contract by calling PlutusDAO's donate().
Lodestar’s plvGLP collateral valuation subsequently increased, and the attacker borrowed almost all the assets from the other seven lending pools of the protocol, nearly emptying Lodestar’s assets.
However, the attacker was still at a loss after repaying the flash loan at this stage. In the following transactions, the attacker redeemed all the GLP pledged through GMX (in the form of ETH). Even after deducting a large proportion of asset management fees during the redemption process, the attacker’s gain on ETH ultimately made up for the losses generated by the primary attack transaction, resulting in a profit.
Oracle Module
Lodestar Finance's deployer deployed the GLPOracle contract, 0xba46f854a5b099fcea178c6e7ed047baffece5ac. Its price of plvGLP follows the equations:
When we compare the plvGLPPrice and its calculation basis before and after the attacker's donation, we can observe that the price instantaneously increased by 1.688 times. The main difference is that the plvGLP.totalAssets() value increased by 5620813.9188, while plvGLP.totalSupply() did not increase accordingly. Another factor that affected the plvGLP price is that the GLPPrice remained unchanged before and after. The token flow graph visualized by EigenTx reveals that the plvGLP contract didn't issue any new tokens throughout the entire process. However, plutusDAO minted new plsGLP tokens from the plsGLP contract rather than plvGLP and transferred them to the plvGLP contract.
Two Redeem Transactions
Tx1: Stake 3,814,441.16 plvGLP to the GlpDepositor contract, redeeming 6,812,534 fsGLP (72.2%).
EigenTx: https://eigenphi.io/mev/eigentx/0x867ef18fb824e7c8d0427e026567cd9877fa3683772730a7ab3745c216960075
Tx2: Unstake and redeem, obtain 4527.67 ETH.
EigenTx: https://eigenphi.io/mev/eigentx/0x9c1785fd3e7c05bd3f1a7cdcfb2bab5ca91dee8d7dcf3d72c58643738e54ca85
Profit and Loss
The table below displays the Profit and Loss (PnL) of various parties based on the token flows that happened during the entire attack process.
A Tokenomic Trilemma View
Based on our proposed Tokenomic Trilemma, the Lodestar exploit falls into Category 1, where the attacker exploited the issuance mechanism of the plvGLP token, causing the market price to deviate from the corresponding value of underlying assets after the critical attack operation. The above diagram illustrates the process as a shift of plvGLP's condition from state a to b. However, from Lodestar's perspective, the oracle remained unaware of this state shift and continued calculating its quote based on the original price anchoring conditions of plvGLP.
The attacker borrowed a significant amount of plvGLP at market price, deposited it back into the lending protocol before the donation, and then attacked the plvGLP issuance mechanism through the function donate() to elevate the collateral's valuation. This action allowed the attacker to borrow excessive amounts of assets.
The Tokenomic Trilemma framework aims to demonstrate that a token faces a trilemma in achieving three conditions simultaneously: free tradability, anchored price, and independent issuance. Risk often arises when exploiters breach any one of these token conditions, leading to a change in its state. The framework helps us comprehend the underlying causes of risk from a tokenomic perspective and understand the limitations of our ability to address such issues. We also aim to collaborate with industry experts to develop a more comprehensive risk management solution.
Follow us via these to dig more hidden wisdom of DeFi: