1 Builder, 1 Searcher, 6 Sandwiches in 5 Minutes Causing $714K Losses
Tracking the MEV Spree Patterns, Profits, and Post-Attack Behaviors
Unseen Sandwich Blitzes
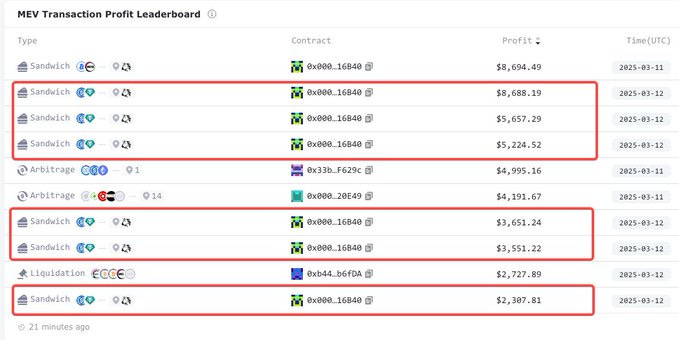
Last Wednesday, March 12, we noticed six of the top ten MEVs in 24 hours were juicy sandwiches using the same pattern.
Over just five minutes, six such attacks were executed, leading to a staggering $714K in victim losses. The benefactors of these attacks, identified as a builder known as “bob-the-builder.eth” and a searcher labeled “6B40,” profited substantially, with the builder netting 220 ETH and the searcher earning more than $29K.
Let’s take a deep dive at one notable instance of them.
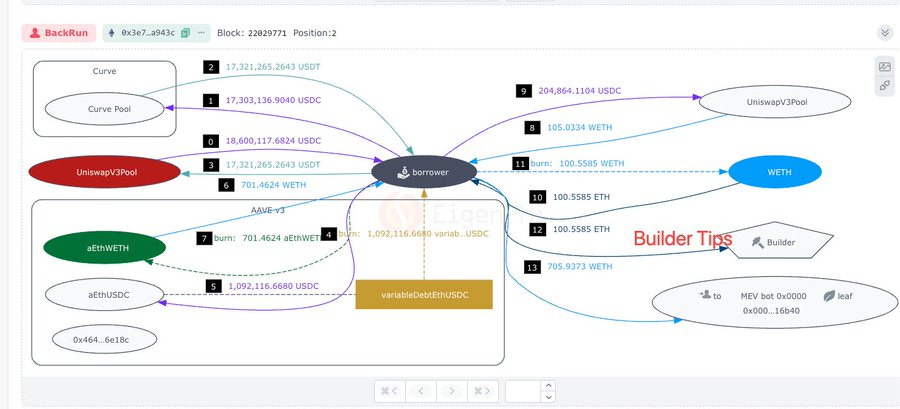
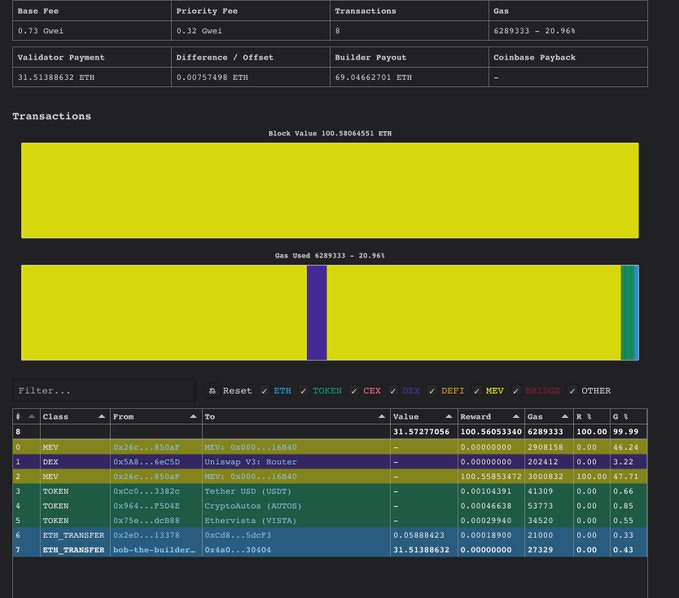
The token flow chart below is the token flow of the sandwich, seemingly causing the user $215.5K.
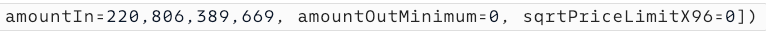
The victim attempted to swap 220.8K USDC for USDT.
However, while using Uniswap V3’s Router, based on the transaction detail on Blocksec’s phalcon, the slippage of the swap, shown as sqrtPriceLimitX96, was set to 0, telling everyone that it would accept any swapping price.
Upon detecting the victim's swap intent in the mempool, the attacker borrowed 1.1 million USDC from Aave using 701 WETH as collateral. They then exchanged 18.65 million USDC for 17.58 million USDT, significantly altering the pool’s rate.
This manipulation caused the victim to receive only 5,273 USDT, while the attacker repaid their Aave debt and secured an $8,688 profit, tipping bob-the-builder 100.5585 ETH.
Different block, different victim, same searcher, same builder. In this sandwich in Block 22029751, the user only received 3,658 USDT for 142K USDC. And the bob-the-builder received 63.6413 ETH as tips.
The same pattern occurred in four additional attacks during the same five-minute span, impacting blocks 22029746, 22029749, 22029751, 22029753, 22029756, and 22029771.
Union Between the Chef and the Builder
In every instance, “bob-the-builder.eth” emerged as the exclusive block winner, collecting a total of 320.65 ETH from these events. Remarkably, in block 22029771, just eight transactions were logged, highlighting the coordinated aspect of these attacks.
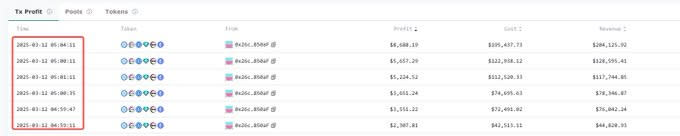
The table below examines the PnL of these six attacks.
Uninformed Tradings’ Path
Next, let’s tour how the order flows went through the MEV supply chain.
We will use the sandwich MEV causing $195K as the example since all six follow the same pattern.
On Mempool.guru, we can see that the user’s transaction was sent to the public mempool, which is enclosed by two private transactions, the frontrunning one and the backrunning one.
Block 22029771 page On Payload.de shows that three builders were bidding on this block: Beaverbuild, Titan, and bob-the-builder, which is labeled as “<unknown>.”, And the bidding amount was pretty close. So, it’s highly likely that the searcher sent its sandwich bundle to all three builders for inclusion.
To summarize:
The uninformed user employed Uniswap V3’s router to swap 220.8K USDC for USDT with the slippage set as 0, which was broadcast to the public mempool.
The sandwich bot 6B40 detected this naive swapping signal in the public mempool, prepped the frontrunning and the back-running transactions, bundled the user swap, and sent the bundle to builders via private channels.
Three builders received the bundle and bid their right to build the block via relays, and bob-the-builder won with the highest payment for the validator.
The selected validator proposed the block, and it was accepted on-chain.
All six sandwiches’ related data are shown in the table below.
A Lesson Learned, a Million Deposited
The attacks happened on Mar 12. The next day, all the 6 EOAs being attacked started another round of trades, with better understanding this time.
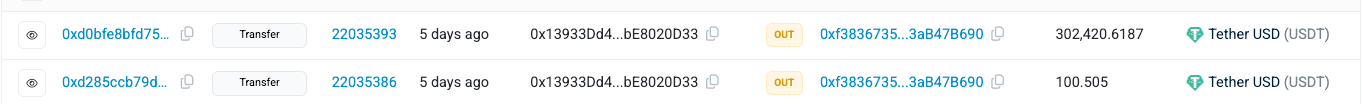
On Mar 13, we can see that 3 of the 6 EOAs transferred assets to the EOA 0xf383, which later deposited a large amount of USDT to the Compound protocol.
Before the depositing, EOA 0x1393 transferred over 302K USDT to EOA 0xf383.
Other than withdrawing from the squeezed Uniswap v3 USDC/USDT pool, EOA 0x1393 also used Uniswap V3 Router to swap 74K USDC for USDT, using the public mempool.
Only this time, it set the right slippage, that’s about 0.084%.
The other 3 EOAs involved during the attack also undertook similar actions on Mar 13.
Before transferring 201K USDT, EOA 0x08eB did the same thing as EOA 0x1393 without being sandwiched.
Adding all the USDTs supplied to the Compound, you would reach 1 million. The dust now seems settled.
Visit this spreadsheet for all the detailed data about each sandwich and summaries mentioned in this post.
Unboxing Bob-the-builder
We have mentioned that bob-the-builder is the one who built all the six blocks involved. Let’s take a close look at his financial gains during the incident.
Out of the six blocks with the six sandwiches, a total of 732.6K USDC is set to be swapped, resulting in 18.6K USDT received.
Bob-the-builder received 320 ETH, worth $621K.
Another significant gain was the 100 ETH received by the proposers of these six blocks, worth about $194K.
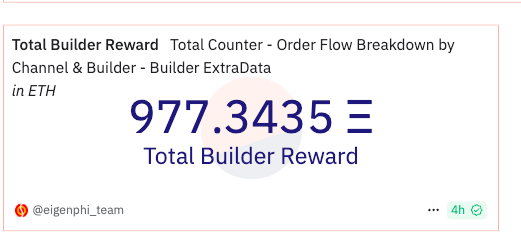
In total, bob-the-builder pocketed 220 ETH, worth $427K, in 5 minutes. From 2025 until Mar 17, bob-the-Builder has received more than 977 ETH as Builder Rewards.
Since its debut in Jan 2024, bob-the-builder has taken 2.6K ETH. The past Feb and the ongoing March are the best months.
It’d be intriguing to dive into how bob-the-builder had such a blast in February. Please stay tuned and leave your comments.
Meanwhile, the MEV dark forest awaits the next uninformed trader.
You can click this link or open https://bit.ly/hfdefi to download the free ebook Head First DeFi, Decoding the DNA of Crypto Transactions & Strategies. We are adding more intriguing cases in 2024. Let us know if you want to be part of it.
Follow us via these to dig more hidden wisdom of DeFi:
EigenTx | Website | Discord | Twitter | YouTube | Substack | Medium | Telegram